Know where to focus your security investments.
Making the right security investments is all about visibility. With Cyber Risk Programs, you get a robust view of your security landscape. By integrating our intelligence with multiple security data sources, you can aggregate, display, and score information in a way that’s easy to understand.
What is Cyber Risk Management?
Cyber Risk Management consists of evidence-based risk assessments and consulting designed to address a wide spectrum of organizational cyber security risk concerns including potential threats, weaknesses and vulnerabilities. They measure the effectiveness of customer cyber security risk controls, quantifies cyber risk in business relevant or financial terms, and provides prioritized risk reducing recommendations and consultative support.
How does Cyber Risk Programs work?
Cyber Risk Programs assess your security posture using risk assessments, quantified scoring algorithms, detailed dark web findings, and proprietary data from our threat intelligence library. This gives you the data to identify security gaps and evaluate where you need to focus, all leading to more informed business decisions. Verizon has over two decades of experience in delivering cyber security and risk assessments globally to both commercial and public sector clients.
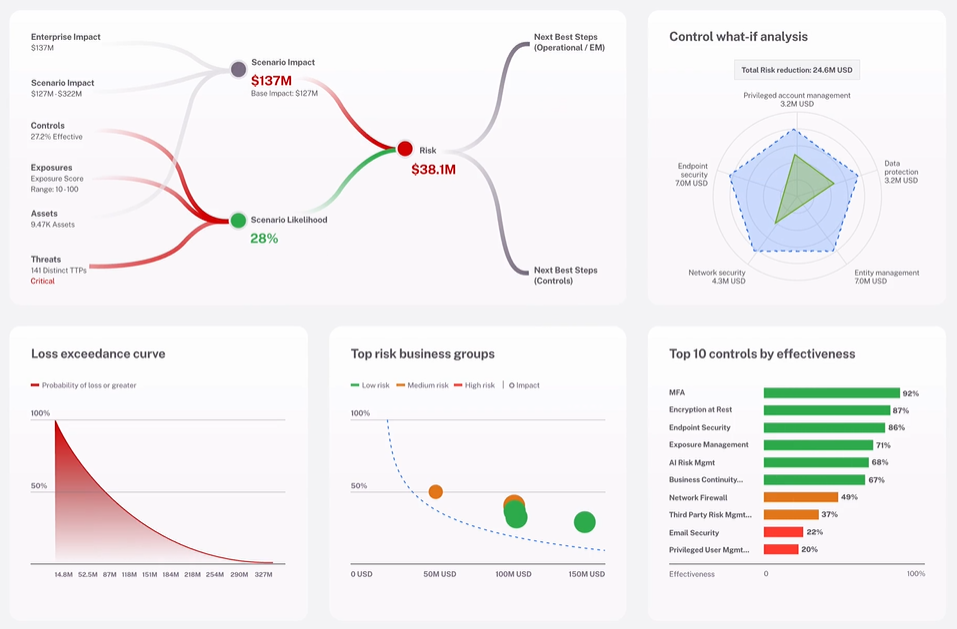
Add on Cyber Risk Quantification.
Quantify cybersecurity risks in financial terms and produce reports that empower CISOs to effectively communicate risk exposure, mitigation strategies.
Know your score.
Cyber Risk Programs deliver executive-level reporting while allowing security analysts to drill down for specific details, helping IT teams save time while maintaining flexibility for various audiences' view.
Features & Benefits
With Cyber Risk Programs, you can get the data to identify security gaps, evaluate where you need to focus and monitor progress over time. Other features and benefits include:
Risk Assessments.
A suite of risk assessment activities that when packaged together help your organization address foundational cyber security strategy competencies, confidentiality, integrity and availability.
Security scoring.
Evidence-based scoring that reflects your risk posture. Scores can be used to provide cyber risk metrics to auditors, stakeholders, cyber insurance providers and business leaders within your organization.
Vendor Risk Monitoring.
Open-source cyber risk intelligence pertaining to your existing and potential vendors.
Rethink Risk with Verizon's Cyber Risk Programs
Verizon's Cyber Risk Programs bring objective, data-driven, quantifiable risk analysis to our customers risk-management strategy. With multiple assessments and custom and tailored options available, we can help customers protect their organizations with a solution that best meets their business needs regardless of size or market. We also provide a cutting-edge Cyber Risk Dashboard and a tenured team of delivery consultants to every customer engagement.
FAQs
Cyber risk monitoring is the continuous process of identifying, assessing, and tracking potential cyber threats and vulnerabilities to an organization's assets and data. It's a proactive approach to managing and mitigating cyber risk, aiming to stay ahead of potential attacks and minimize their impact.
Systematic processes that organizations use to identify, evaluate, and prioritize potential threats and vulnerabilities to their information systems, data, and critical assets. Leverage identification of vulnerabilities within your current environment, coupled with actionable remediation recommendations. The ultimate goal is to understand the potential impact of these risks and implement effective security measures to mitigate them.