Additional 2025 DBIR research on credential stuffing
By Philippe Langlois, Lead Data Scientist, Verizon Business
The Verizon Data Breach Investigations Report (DBIR) already weighs in at over 100 pages annually, which means the team is often unable to showcase the research conducted on any given topic in its entirety. In this article we would like to highlight some of the aforementioned research conducted by the team regarding credential abuse and credential stuffing that we could not fit into the report itself.
However, if you are in a hurry, a bird's-eye view of our key findings for this article are as follows:
- The use of compromised credentials was an initial access vector in 22% of the breaches reviewed in the 2025 DBIR.
- Infostealer malware infection data shows that, in the median case, only 49% of a user’s passwords across different services were distinct from each other.
- In analyzing SSO provider logs, we found that the median daily percentage of credential stuffing accounted for 19% of all authentication attempts. This number goes as high as 25% in enterprise-sized companies, while small businesses experience it at 12%.
Credential Stuffing, the less popular Thanksgiving side dish
As regular readers of the DBIR, you are no doubt aware (if we did our jobs correctly) of the high number of breaches that involve the use of compromised credentials as the initial vector, which currently accounts for 22% of our breaches. We offer Figure 1 to refresh your memory regarding what we discussed in this year's report.
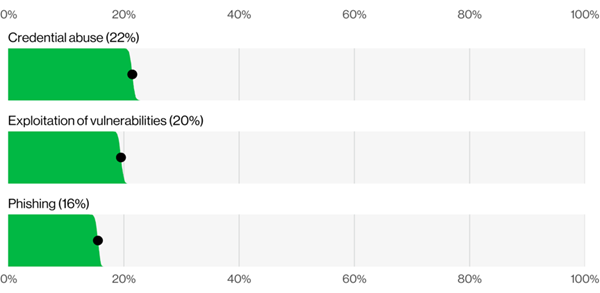
Figure 1. Known initial access vectors in non-Error, non-Misuse breaches (n=9,891)
While we have good insight into credential abuse, we don’t always know where all those credentials are coming from in these types of incidents. However, a couple of common sources include: credentials compromised by infostealers, creds that were compromised via phishing attacks, or that were obtained via other means. We hate to assign homework, but if you want to earn extra credit you can learn more about infostealers by examining our analysis on page 54 of the 2025 DBIR.
The use of poor authentication practices or weak and stolen credentials don’t just affect our organizational users, but can also pose a risk to customers. A customer who reuses their passwords, which are then compromised in other breaches, could find their accounts taken over via credential stuffing at a different organization entirely. It is a large-scale problem, and any organization can be impacted by it. Victims range from verticals one might expect, such as gaming platforms, to (somewhat surprisingly) a classic American jeans company.
(Re)Users Beware
Credential stuffing is an attack against an organization’s authentication system that leverages a list of known compromised username and passwords. These lists are often collected, shared and sold as a “ComboList” and can be easily found in most marketplaces or cybercrime related Telegram channels. In addition to the ComboLists, attackers also often leverage proxies to help hide the origin of the attack, attempt to bypass certain security controls, and automate their illicit workload with configuration files which detail the authentication endpoint being targeted along with any associated headers.
Given that these types of attacks will only try to authenticate once against a specific user account, and can hide their attack by modifying headers, they are often successful in hiding the attacks amongst regular authentication traffic. However, at the end of the day, there are two main weaknesses that enable these credential stuffing attacks to be successful. The first is the bad habit of users reusing their passwords; and secondly, Multi-Factor Authentication (MFA) not being leveraged by those users when it is available. MFA-enablement is not the panacea it used to be in stopping credential abuse, but it is quickly moving to be considered table stakes in any authentication process one might care about.
When it comes to password reuse, we should all recite the wise password mantra, “Thou shalt use strong and unique passwords.” However, when examining actual behavioral patterns, we find that while users can recite the mantra from memory, following it in every day practice is a different story. When we looked at users whose systems were infected with infostealer malware (which focuses on stealing saved credentials), we found that, in the median case, only 49% of a given user’s passwords across different services were distinct from each other (Figure 2). So, to put it simply, some of those keys may open a lot of doors.
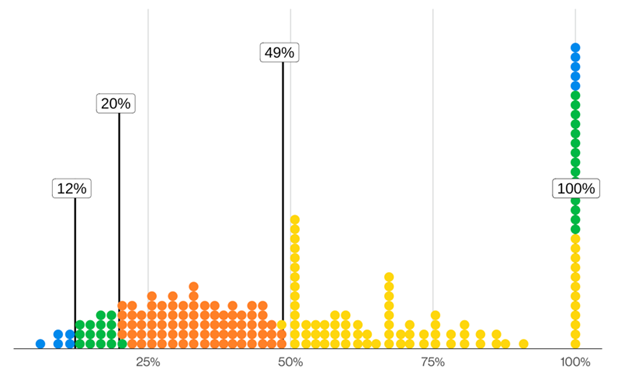
Figure 2. Percentage of unique saved passwords per compromised device found in infostealer logs (n=14,742 - each dot is 73.71 users)
This is why these ComboLists are so valuable to attackers–they can try them against different services and there is a good chance that a user has reused their password in multiple places.
Low and Slow
One of the more insidious things about credential stuffing is the variety and breadth of potential targets. Some folks might think that their users aren’t at risk, but there’s actually a wide variety of different organizations that are being targeted–it’s not just the major streaming platforms that need to worry. By the powers of automation and scale, it likely costs very little to an attacker to simply try each password against numerous websites.
By looking at authentication logs associated with SSO providers, we were able to identify how prevalent credential stuffing attacks are in terms of overall authentication attempts.
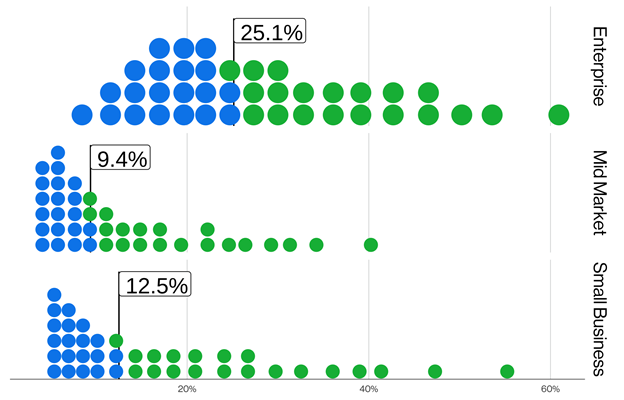
Figure 3. Percentage of authentication events that are credential stuffing attacks grouped by organization size (n=2,301)
For these customers, the median daily percentage of credential stuffing accounted for 19% of all authentication attempts over a period of two years. We break out this finding by organization size in Figure 3. Even organizations that are classified as small have about 12% of authentication attempts being an active credential stuffing attack. For an even more shocking number, the highest percentage we found for credential stuffing on a single day is 44%, which is just under half of all authentication attempts being attributed to these attacks.
Recommendations
Now that we have painted this rather gloomy picture (you’re welcome), what can you do to help protect your organization against these types of attacks?
- Promote and incentivize the adoption of MFA for your users. Various organizations have found ways to promote good cybersecurity practices, such as encouraging MFA adoptions by providing rewards for the users who turn it on. https://www.riotgames.com/en/news/get-rewarded-for-enabling-2fa
- CAPTCHAs can help prevent automated requests, but there are services and tools that can bypass some of these.
- Implement some of the architecture recommendations from OWASP https://cheatsheetseries.owasp.org/cheatsheets/Credential_Stuffing_Prevention_Cheat_Sheet.html
If you are interested in learning more about infostealers and credential abuse, we suggest taking a look through the Verizon DBIR (verizon.com/dbir). The 2025 edition is there waiting for you to (re-)read it.

Philippe Langlois is currently working as the lead data scientist and one of the co-authors of the Verizon Data Breach Investigations Report (DBIR). Prior to joining Verizon, he worked at CIS leading various data driven projects, such as the CIS Controls and the MS-ISAC Nationwide Cyber Security Review. When not working or recreationally programming, he enjoys the great outdoors of Upstate New York with his wife, son and dog.