Simplifying and Demystifying Cybersecurity: Why Your Home Security is a Good Analogy
Author: Thomas Raschke, Sr. Security Product Marketing Manager, Verizon Business
Date published: October 15, 2025
Cybersecurity challenges are faced by almost every organization. While the digital world may seem confusing, cybersecurity language and concepts can be simpler than you think if you compare it to familiar concepts like home security. Your home, much like an organization's digital assets, represents something valuable that you want to protect. The measures you take to secure your home can be directly similar to the methods used in cybersecurity.
Mapping the Physical World to Cyberspace
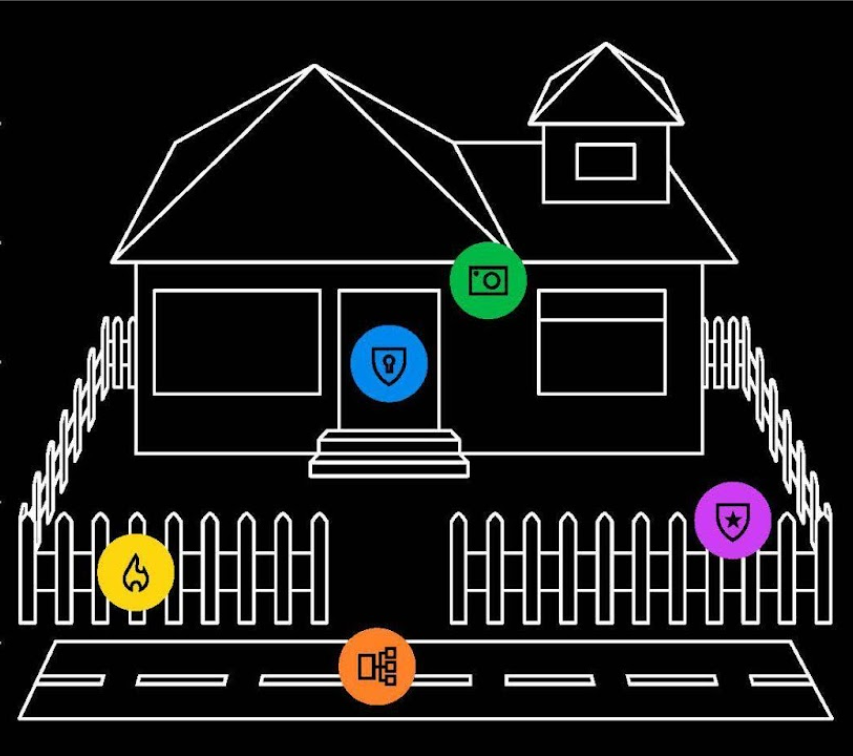
The similarities between protecting your house and protecting your digital assets are striking, making complex concepts more approachable.
| Home Security Element (Physical World) | Cybersecurity Equivalent (Digital World) |
|---|---|
| Doors and locks control who enters your house. | Access management and passwords control access for organizations, confirming that access is granted to the right people at the right time and preventing unauthorized credentials. |
| Streets and public spheres are where strangers roam. | Networks and the internet can be overwhelmed by fake traffic resulting in unavailability, which is known as a Denial-of-Service cyberattack. |
| Fences and walls are the natural boundaries. | Firewalls help protect the cyber perimeter and help prevent attacks such as port spoofing. |
| Cameras identify activities like a thief or a delivery. | Security monitoring and detection generate logs that can track hidden threats, such as login attempts leading to data breaches. |
| The alarm company responds quickly to a detected threat. | A security operations center (SOC) responds to threats, starts cleanup, recovery, and improvement processes. The faster the response, the better the chances of containing an attack. |
Understanding Common Threats and Attack Vectors
The threats faced in cyberspace often mirror physical intrusions.
- Credential Theft: Thieves breaking in with your keys or passcodes is analogous to attackers using someone’s credentials to "walk right in."
- Ransomware Attacks: This major type of blackmail in cyberspace is like someone replacing all the locks on your house while you are away and demanding money for the new keys. Verizon can help mitigate such attacks.
- Denial-of-Service (DoS) Attacks: This occurs when a criminal clogs the streets so your guests can't arrive, preventing access to organizational resources.
- The Human Element: One of the biggest threats to security is often caused by humans (i.e., you). We leave the garage door open or share keys, making the human element the weakest link in all security, which can also be true for cyberspace.
- The Extended Threat Surface: Threats can come from a growing number of areas, including Mobile and IoT devices, which contain valuable information and are not always behind the safe walls of your main network.
Applying the NIST Cybersecurity Framework
The National Institute of Standards and Technology (NIST) has developed a widely adopted 5-point framework to help businesses outline where to focus their time and money for cybersecurity protection.
- Identify: This step involves finding holes and weaknesses in your security posture. Organizations often hire experts to perform services such as penetration testing or compliance and risk assessments like those offered through Verizon’s Cyber Risk Programs or Governance, Risk, and Compliance (GRC) portfolio.
- Protect: Apply common sense security, such as keeping doors locked. This involves using network and security solutions like SASE (Secure Access Service Edge)—a cloud-based framework that brings network and security together or Zero Trust architecture which operates on the principle: "Trust no one and verify all."
- Detect: You must know the difference between a thief/hacker and a delivery guy/legitimate business user. Services such as Managed Extended Detection and Response (MxDR) with Accenture can help organizations stop potential intrusions and identify suspicious activity and patterns.
- Respond: React the right way to previously detected incidents. Many organizations rely on security operations center services, such as Advanced SOC Services or the Cyber Security Incident Response Team (CSIRT), to call the authorities or help handle the incident.
- Recover: After a breach, clean up, get back to normal, and close the holes that enabled the break-in. Organizations often rely on incident response experts, such as rapid response teams, to react swiftly and help improve the overall security posture.
Starting the Conversation
Cybersecurity has become a critical boardroom topic because poor or inadequate security can lead to disastrous results. To help improve your security posture, organizations should evaluate their security risks and look into solutions for secure connectivity such as using network-embedded security capabilities like DDoS, SASE, and Zero Trust.
By reviewing this analogy, understanding the concerns of your audience, and knowing the latest security concepts — like social engineering (e.g., getting someone to voluntarily hand over keys) — you can start a helpful conversation about addressing and helping mitigate your organization's cybersecurity risk.

Thomas Raschke, Sr. Security Product Marketing Manager, Verizon Business
Security professionals frequently encounter the challenge of helping simplify complex cybersecurity concepts for non-technical audiences, such as executives, clients and even family members. Bridging this knowledge gap is crucial for effective communication, getting support for security projects, and helping everyone become more security-aware. The following analogy offers a highly relatable and easily understandable framework, comparing cybersecurity principles to the familiar concept of home security: