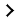-
Overview
-
Cyber Risk Monitoring changes the way we talk about security. It allows you to understand your organization’s security posture and threat environment. By integrating multiple security data sources, the service provides you with a 360-degree view of your company’s security posture (when all three levels are purchased), with actionable data that allows you to focus on a clear action plan, which will deliver a quantifiable return on your security investments. This service is designed for consumption from the board level to the security operating team level. In addition, the service benchmarks your company against its industry and allows for the monitoring of suppliers’ and/or partners’ Outside-In security posture by leveraging a third-party scoring method that has become a risk requirement in some industries, and a best practice in other industries.
Cyber Risk Monitoring provides a rating of your organization's outside-in, inside-out, and comprehensive security postures based on an assessment of your internal, external, company culture and policy risk vectors, combined with Verizon's proprietary insights from the Data Breach Investigation Report (DBIR).
-
Your Verizon team
-
Your Cyber Risk Monitoring team will help guide you through the contract signature process to the eventual provisioning of your Cyber Risk Monitoring service.
Account Executive
The Account Executive is responsible for the sale of Cyber Risk Monitoring to you. They are also your initial POC for any questions regarding the purchase and implementation of the Cyber Risk Monitoring.
Project Manager
The Project Manager assists with user account provisioning and sends the Welcome Letter.
Executive Consultant
An Executive Consultant will be assigned to help you navigate through your Cyber Risk Monitoring scores, discuss strengths and weaknesses driving the score, and to answer any questions you may have. The Executive Consultant will be assigned to you for as long as you remain a Cyber Risk Monitoring customer, with the goal of helping you gauge and address your cyber risk.
-

-
To successfully deliver Cyber Risk Monitoring, there are some activities that must be completed by both Verizon and you. Our goal is to keep you informed and aware of all the steps.
Verizon steps
Verizon will provide the full contact details for the Account Executive, the Project Manager, and any other relevant Verizon contacts and will take the following actions to provide a smooth implementation of Cyber Risk Monitoring:
-
- Upon successful submission of the Cyber Risk Monitoring order, the Project Manager will be your lead contact for the engagement.
- The Project Manager will provide his or her contact details, and other information associated with the Cyber Risk Monitoring order.
- The Project Manager will coordinate all project components from start to finish as part of the service.
- Verizon will send an email requesting the names and emails of all users who will need access to Cyber Risk Monitoring. Verizon will also provide a Welcome Letter (via email) from the Project Manager that will describe how to access Cyber Risk Monitoring.
- Verizon will establish your user account within the Cyber Risk Monitoring portal.
- For Level 2, after access is established, the Project Manager will provide a data integration quick start guide and specific vendor integration guides. If additional endpoint agents are purchased, they will schedule a Customer Kickoff Call with you and other Verizon team members and will provide implementation status updates during weekly calls and communications on an as-needed basis.
- If additional endpoint agents are purchased, they will schedule a Customer Kickoff Call with you and other Verizon team members and will provide implementation status updates during weekly calls and communications on an as-needed basis.
- Verizon will provide verification via email that your portal was properly created and set up.
For Level 1 customers:
The implementation will be handled via the Project Manager and the automated email instructions.
- The Project Manager will engage the Managed Security Services (MSS) Provisioning team to configure your account(s).
- The Project Manager will send you a Welcome Letter.
- An automated email for your self-registration will be sent.
- For new CRM customers, the Professional Services Delivery team will engage you to schedule a one-hour acclimation meeting and communicate standard deliverables.
- This does not apply to customers upgrading.
Note: Any additional consulting constitutes a paid Professional Service engagement.
For Level 2 customers:
- The Project Manager will engage the Managed Security Services (MSS) Provisioning team to configure your account(s).
- The Project Manager will send a Welcome Letter, a data integration quick start guide and specific vendor integration guides.
- An automated email for your self-registration will be sent.
- If additional endpoint licenses are purchased, the Project Manager will work with the Install Team to set up a new Cylance tenant and post the agent installation files into the portal.
- Before the kickoff call, Verizon will provide the Deployment Guides and install instructions (via the Cyber Risk Monitoring customer packet) to assist with the Verizon provided agent endpoint installation. (This information can also be found on the Integrate Data Sources page in the Cyber Risk Monitoring portal.) This documentation provides device deployment recommendations, as it is critical to choose a set of endpoints that represents the whole of the environment so a more realistic risk assessment can be obtained by Cyber Risk Monitoring. E.g. if 30% of your endpoints run Linux then install 30% of your agents on endpoints running Linux.
- The Project Manager will schedule a kickoff call with you and the install team. During the call, the install team will recommend how to distribute Verizon provided Cylance software within your network and will provide a customer packet (installation instructions, FAQ, destination IP addresses, etc.). Verizon will provide the contact details for the person you should notify when the provisioning steps have been completed.
- Verizon will test the data collection from the endpoints.
- Verizon will evaluate possible connectivity issues on the endpoints, working in conjunction with the customer’s technical team, to determine the root cause of the connectivity issue deployed agents.
- Collect Data
- Once the customer provided connection information is submitted and/or endpoint agents are deployed, Verizon will begin collecting data from one or more endpoint data sources, using the established Cyber Risk Monitoring process/tools.
- For new CRM customers, the Professional Services Delivery team will engage you to schedule a one-hour acclimation meeting and communicate standard deliverables.
- This does not apply to customers upgrading.
Note: Any additional consulting constitutes a paid Professional Service engagement.
For Level 3 customers:
- The Project Manager will engage the Managed Security Services (MSS) Provisioning team to configure your account(s).
- The Project Manager will send you a Welcome Letter.
- An automated email for your self-registration will be sent.
- Your assigned Security Analyst will contact you to begin scheduling the assessments. The Analyst will work through each of the assessments, which are performed quarterly for the term of the contract
- For new CRM customers, the Professional Services Delivery team will engage you to schedule a one-hour acclimation meeting and communicate standard deliverables.
- This does not apply to customers upgrading.
- Level 3 customers are provided 100 hours of Professional Services support.
Note: Any additional consulting constitutes a paid Professional Service engagement.
Customer Steps
The following steps on your part will also lead to a successful and timely delivery of your Cyber Risk Monitoring:
Level 1
You will receive the Welcome Letter detailing the self-registration process for accessing the Cyber Risk Monitoring portal.
- Please proceed through the self-registration process to gain access to the Cyber Risk Monitoring portal.
Level 1 Customer action
- Please respond to the initial email request for user account information including names and email addresses.
Note: Upon receipt of your Welcome Letter (via email), please follow the instructions for accessing Cyber Risk Monitoring via the Unified Security Portal (USP). (If you are upgrading from another level, there is no need to re-register.)
Note: Within the USP are extensive tool tips and an integrated help guide available to assist you in accessing and managing Cyber Risk Monitoring.
Note: If you experience issues with onboarding, you will contact [email protected]. You may also contact the Security Sales Representative during business hours to answer any questions.
Level 2
You will receive the Welcome Letter detailing the self-registration process for accessing the Cyber Risk Monitoring portal.
- Please proceed through the self-registration process to gain access to the Cyber Risk Monitoring portal.
Level 2 Customer action
- Please respond to the initial email request for user account information including names and email addresses.
Note: Upon receipt of your Welcome Letter, quick start guide and specific vendor integration guides, (via email), please follow the instructions for accessing Cyber Risk Monitoring via the Unified Security Portal (USP). (If you are upgrading from another level, there is no need to re-register.)
- Please use the quick start guide and vendor integration guides to provide connectivity information for your data sources. Once the information is provided, the data pulls will automatically start within 24-hours.
Note: Within the USP are extensive tool tips and an integrated help guide available to assist you in accessing and managing Cyber Risk Monitoring.Note: If you experience issues with onboarding, you will contact [email protected]. You may also contact the Security Sales Representative during business hours to answer any questions.
If additional endpoint licenses are purchased, the Project Manager will
- Provide a customer packet (via email) prior to the kickoff meeting that includes a deployment guide, customer checklist, and contact information for your Project Manager and Executive Consultant
- Schedule a kickoff call with the following objectives:
- Cyber Risk Monitoring team introductions, roles, and responsibilities
- Expectations of Verizon and your organization
- Validate the project scope and services
- Discuss timelines and deliverables
- Outline next steps
- Your Install Team will provide instructions on the deployment of the Verizon provided agents, and will share recommendations for the distribution of the agents within your network.
Level 2 Customer action if aditional endpoints are ordered:
- Please ensure a local contact is present on the due dates provided to avoid re-scheduling and potential service downtime.
- Please complete the customer checklist (from the customer packet) and return it to your Verizon Project Manager prior to installing the Verizon provided Cylance agents.
- Please use the deployment guide(s) (again, from the customer packet) to install the Verizon provided Cylance agents on your endpoints, and once deployed, please contact the Install Team to alert them that the software has been loaded on all the endpoints so they can verify that the endpoints are reporting back to the servers.
Level 3
You will receive the Welcome Letter detailing the self-registration process for accessing the Cyber Risk Monitoring portal.
- Please proceed through the self-registration process to gain access to the Cyber Risk Monitoring portal.
Level 3 Customer action
- Please respond to the initial email request for user account information including names and email addresses.
Note: Upon receipt of your Welcome Letter, (via email), please follow the instructions for accessing Cyber Risk Monitoring via the Unified Security Portal (USP). (If you are upgrading from another level, there is no need to re-register.)
Note: Within the USP are extensive tool tips and an integrated help guide available to assist you in accessing and managing Cyber Risk Monitoring.
Note: If you experience issues with onboarding, you will contact [email protected]. You may also contact the Security Sales Representative during business hours to answer any questions.
Available Training
Cyber Risk Monitoring Dashboard training is a 20 minute, self-paced training. The course material covers the following:
- Features and functionality of the Cyber Risk Monitoring Dashboard.
- A high level overview of the three levels offered by Cyber Risk Monitoring.
- A video demonstration and simulation to teach the learner how to navigate and use the Cyber Risk Monitoring Dashboard.
- Cyber Risk Monitoring - Vendor Risk Dashboard training is a 15 minute self-paced course that covers the following items: Benefits of the Vendor Risk Dashboard
- Features and functionality of the Vendor Risk Dashboard
- Basic dashboard navigation
Cyber Risk Monitoring – Portfolio Management is a 30 minute self-paced course that covers the following:
- Portfolio Management overview, features and benefits
- Interactive video simulation
- Optional Scavenger hunt
Customers can access these courses by going to http://customertraining.verizon.com, and searching by the course name. When accessing the customer training web site for the first time, you will be asked for a registration code. The following code is available for your use: ENTVEC4
-
Cyber Risk Monitoring Service Level Options
-
Cyber Risk Monitoring service level offerings include Level 1, Level 2 and Level 3, depending on your organization’s needs.
Level 1
The Cyber Risk Monitoring Level 1 service) starts with an external security risk assessment that combines a risk rating from BitSight; Deep Web, Dark Web and private forum insights from Recorded Future; and the Verizon DBIR threat patterns, which are customized using the BitSight external risk vectors in a prioritized manner based on DBIR insights for your organization’s industry and size.
Level 2
Level 2, which can be ordered separately or combined with other levels, creates a daily internal assessment and risk rating by leveraging metrics collected from within your organization’s network. These metrics use data from endpoints, gathered using Cylance, CrowdStrike, and/or Lookout software agents and data from firewalls using Palo Alto devices running Security Lifecycle Review (SLR) Probe and/or DNS requests from DNS Safeguard/Cisco Umbrella, which identify threats, misconfigurations, and vulnerabilities, and determine your overall security posture and are prioritized based on Data Breach Investigations Report (DBIR) insights for your organization’s industry and size.
Level 3
Level 3, which can be ordered separately or combined with other levels, includes culture and process risk vectors to define your Security Posture. These comprehensive risk assessments are provided based on daily, monthly, and quarterly analyses.
In addition to the integration options, as a Cyber Risk Monitoring customer, with Level 1 you may procure the Vendor Risk Dashboard add-on feature to get an outside-in security posture for your suppliers/vendors and/or target acquisitions. You may also procure Portfolio Management, which embeds the hierarchy of your portfolio companies into the Cyber Risk Monitoring Dashboard, enabling the risk assessment per affiliate company, as well as consolidated views of your organization.
Service Level Delivery Data Sources Level 1 Fully automated outside-in view, daily report via Unified Security Portal (USP) with specific prioritized recommendations BitSight, Verizon DBIR, Recorded Future Level 2 Fully automated inside-out view, daily report via Unified Security Portal (USP) with specific prioritized recommendations Cylance, Crowd Strike, Lookout, Recorded Future, Palo Alto, DNS Safeguard/ Cisco Umbrella Level 3 The culture and process view includes a series of Professional Services-based assessments with specific prioritized recommendations. Verizon Cyber Risk Programs
-

-
The Cyber Risk Monitoring offers a simple self-registration process that makes it quick and easy to begin using the Portal.
Supported browsers – Cyber Risk Monitoring is best viewed through a modern web browser, such as Google Chrome.
Self-Registration and Logging In - Following the Welcome Letter, you will receive an invitation from [email protected] that will include the URL link and instructions for self-registration so you may login to access the Cyber Risk Monitoring portal. Please note that for security reasons, the invitation URL is only valid for forty-eight (48) hours. If you do not register within this timeframe, you will need to contact us (see below).
-
Cyber Risk Monitoring Self-Registration Process
- To begin the Cyber Risk Monitoring self-registration process, please refer to your User Registration Invitation email.
Note that the email may be delivered to your Spam or Junk folder. - Create Account: Enter the requested information under the User Registration Details heading and click Create Account. Username must be unique and cannot contain an email address.
- Login: Once your account has been successfully created, you will be forwarded to a login page. Use your newly created Username and Password to log into the system.
- One-Time-Passcode: Check your email for an email titled Your Verizon Managed Security Passcode. Copy and paste the 8-digit passcode from the email into the One-Time Passcode (OTP) field and click Submit.
- Security Questions: You will be required to select and answer two Security Questions. These questions will be used if you need to unlock your account in the future. After you have selected and answered both questions, click Save & Continue.
- Mobile Authentication: Finally, you are able to sync your smart phone’s Two-Factor App (any iTunes / Playstore supported app) by scanning the provided Quick Response (QR) codes to generate One-Time Passcodes which will be used in the login process.
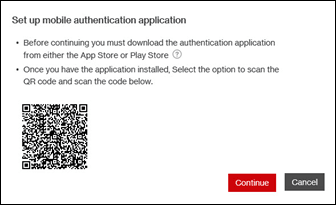
Note: You may choose to Skip Mobile Authentication, resulting in a pop-up window that will allow you to proceed directly to the Cyber Risk Monitoring in the future. If you choose this option, you will use an OTP delivered to your email to login to the portal.
Note: Using Google Authenticator on Android devices is not recommended due to Google’s time synching issue. If you choose to use Google Authenticator on an Android device, please follow the instructions below to ensure your device time is synched correctly.
- Go to the Main menu in the Google Authenticator app
- Tap More > More > Settings
- Tap Time correction for codes
- Tap Sync now
Once the app verifies that the time has been synched, you may use your verification codes to sign in.
Note: The sync will only affect the internal time of your Google Authenticator app, and will not change your device’s Date & Time setting.
- You will be directed to your Cyber Risk Monitoring dashboard page.
Accessing the Cyber Risk Monitoring
Now that you have completed the Cyber Risk Monitoring self-registration process, you may click on the link representing your organization's geographical location to enter your Username, Password, and One-Time Passcode to access Cyber Risk Monitoring going forward:
- For access in the Americas: https://mss-24.verizonbusiness.com/vrr/
- For access in EMEA: https://mss-25.verizonbusiness.com/vrr/
- For access in APAC: https://mss-26.verizonbusiness.com/vrr/
- To begin the Cyber Risk Monitoring self-registration process, please refer to your User Registration Invitation email.
-
Value-added features
-
There are value-added features available with Cyber Risk Monitoring.
Note: Not all options are available at every level, and additional fees may apply. Ask your Verizon Account Team for more details.
Vendor Risk dashboard
This Level 1 add-on service allows customers to monitor the security posture of the vendors and partners they do business with.
- Continuously monitor and quantify the cyber risk of third parties
- Lead intelligent, data-driven conversations with vendors about their security posture
- Increase visibility during M&A activity
- Will be accessed via the Cyber Risk Monitoring portal
Portfolio management
This Level 1 add-on service allows customers to manage and view an executive summary of their related legal entities (i.e. subsidiaries and affiliates).
- View related entities, scores, aggregations, and summaries for your privileged subsidiaries within your portfolio
- Enables seamless navigation within Cyber Risk Monitoring for related subsidiaries
- View a list of user-defined groups that allows you to review information about the group itself, or drill down into a group’s associated subsidiaries and review detailed information for each
Verizon Provided Cylance Additional Licenses
Licenses are available in increments of 25, 50, 100, and 500. Up to a total of 5,000 Cylance licenses can be ordered with Cyber Risk Monitoring. For the best assessment, it is recommended that agents are deployed to 25% of the network’s total endpoints, at a minimum.
Service Issue
Order
Be prepared with the following information:
Service Order Number
Call/Visit
Contact Assigned Account Team
Account Team
Contact Assigned Account Team
Service Issue
Service Assurance
Be prepared with the following information:
Service Order Number
Call/Visit
Contact MSS-CSD at
[email protected], or click Verizon Enterprise Center:
Select Contact Us, select your Country, and then select Support.Account Team
Contact Assigned Account Team
-
If your Company Legal Entity(ies) information is incorrect and/or missing, please contact support at [email protected] to correct the issue.
-
If your company domain (URL) information is missing or incorrect, you can contact MSS-CSD ([email protected]) for assistance.
-
Please contact your Verizon Sales Representative to discuss upgrading your Cyber Risk Monitoring service.
-
To help you get the most value out of Cyber Risk Monitoring, a member of our security practice team will set up a meeting to walk your team through the Dashboard and answer any questions.
-
In order to add new users, please contact support at [email protected]. You will be asked to provide the user’s email address and name. They will be contacted by support with instructions to set up their account.
Services and/or features are not available in all countries/locations, and may be procured from in-country providers in select countries. We continue to expand our service availability around the world. Please consult your Verizon representative for service availability. Contact us.