Overview
Verizon's Trusted Connection is a comprehensive security solution that allows customers to manage access to their SaaS applications. The service provides a turnkey solution that includes mobile and non-mobile devices, network access, security, and application connectivity. All features are managed by an administrator through a dedicated portal.
Trusted Connection is available in two packages to allow customers to choose the level of control they need – Trusted Connection and Trusted Connection Plus.
Operating systems that are supported by Trusted Connection include iOS, Android, Windows, macOS and iPadOS.
Getting Started
Your designated SPOC and users with an Administrator role in the Verizon My Business portal will receive an email with instructions on how to set up Trusted Connection and deploy the Trusted Connection agent to your end users’ devices.
Trusted Connection Setup
As the Trusted Connection Administrator, you are responsible for the initial setup. Simply click on the Trusted Connection link either in My Business portal or access the Trusted Connection portal directly and click “Get started”.
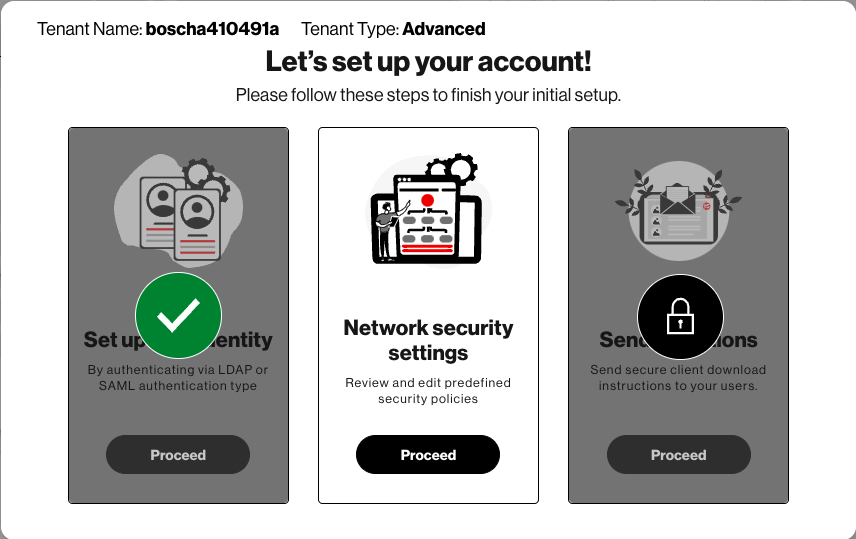
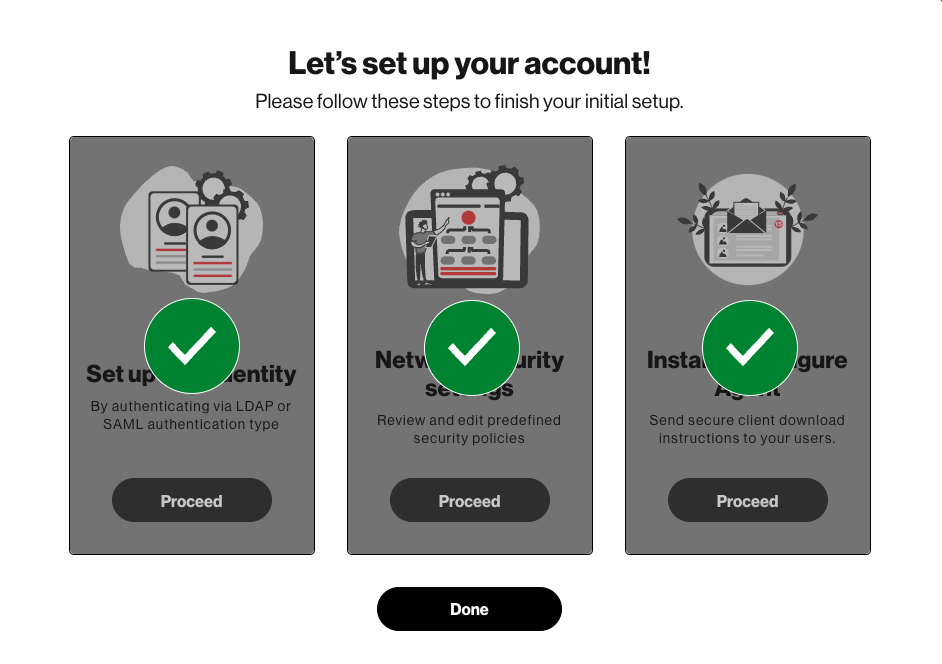
Setting up the service takes three simple steps:
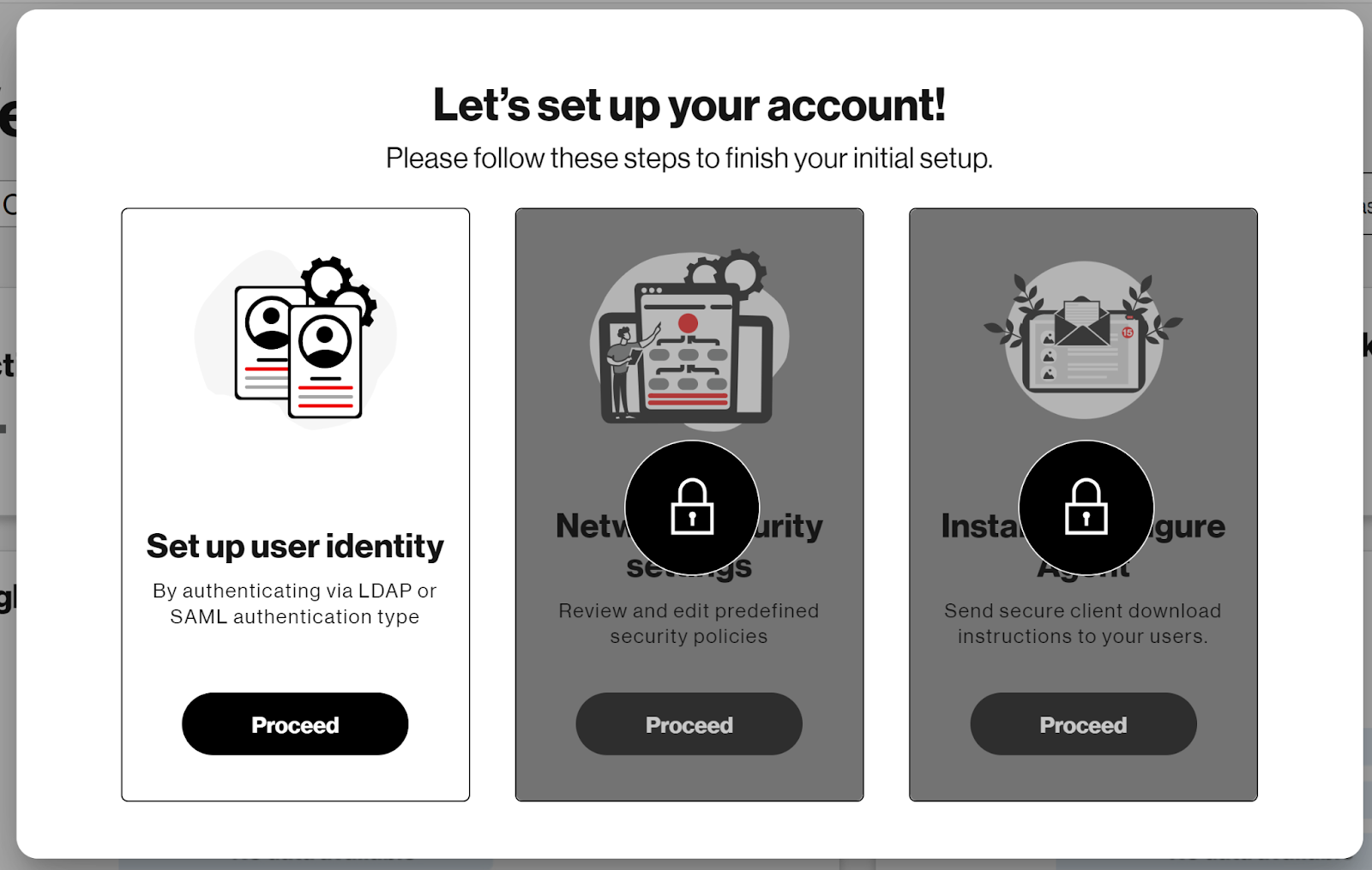
A. Set up user identities
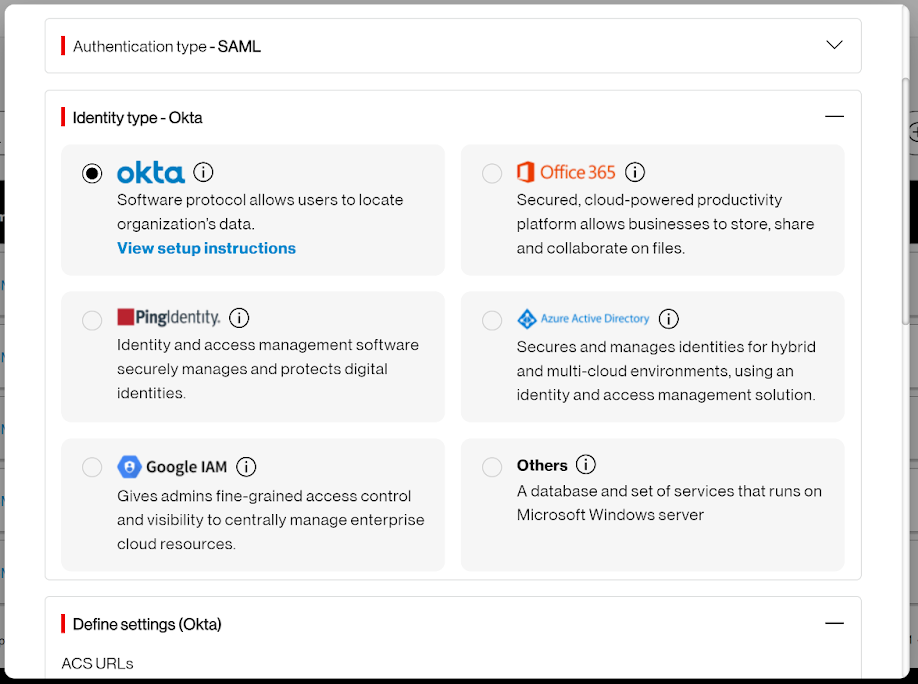
Trusted Connection currently supports many Identity Management (IdP) systems as part of the Bring Your Own Identity Access Provider (BYOID) feature. As long as the system is based on LDAP/SAML, it can be synched to Trusted Connection. Okta Identity Access Management is being used here as an example of how to connect to your system. For a full list of supported IdP, please click here: Identity Access Management and review the FAQ for more Trusted Connection Resources.
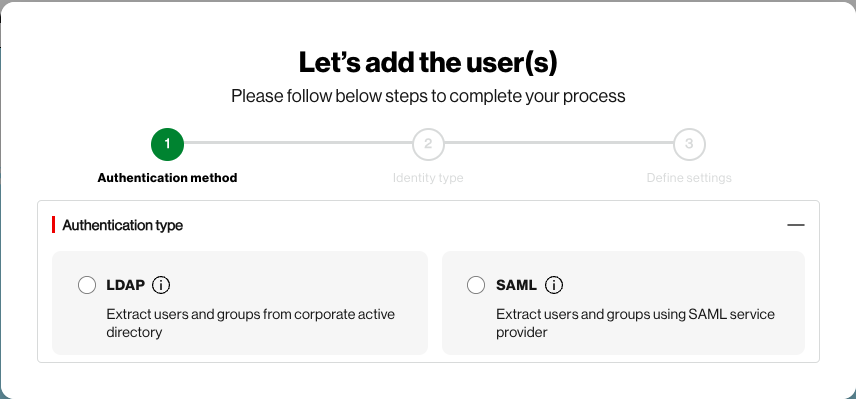
When selecting LDAP with Active Directory, you will need to have the following information:
See OpenLDAP for more details about LDAP requirements.
- FQDN or IP Address
- VPN name
- Port number
- Bind DN
- Bind password
- Domain name Base DN
- SSL mode (optional)
- CA certificate (optional)
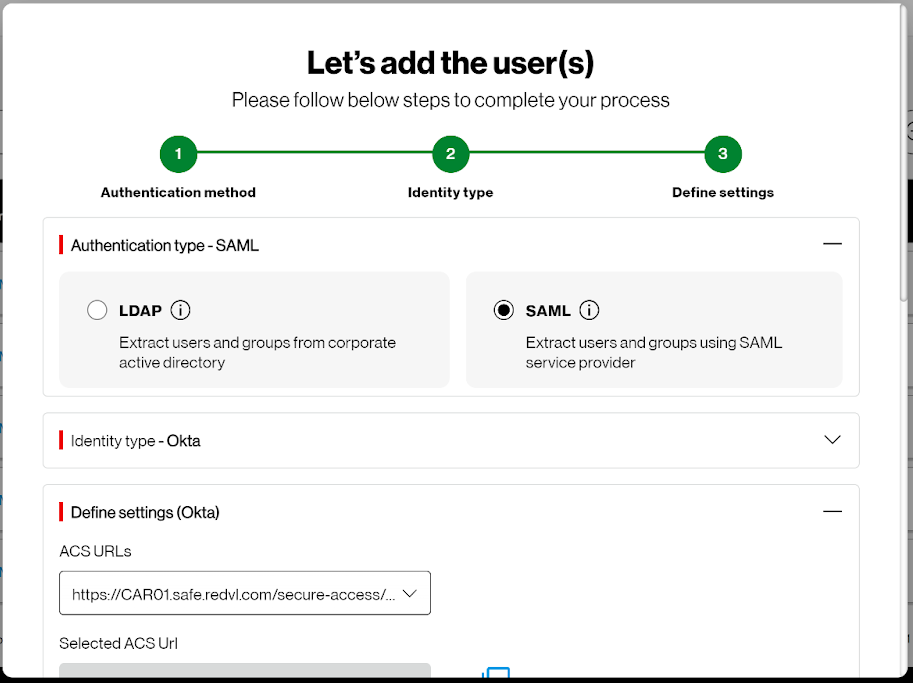
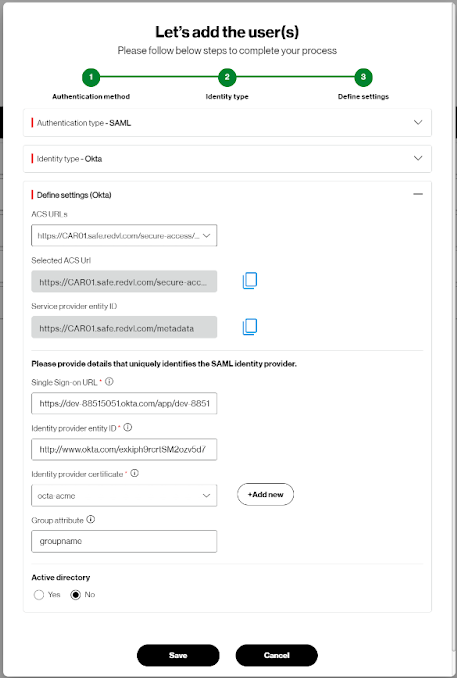
If you select SAML, you will need the following information:
- ACS URLs
- Selected ACS Url
- Service provider entity ID
- Single Sign-on URL * mandatory information
- Identity provider entity ID *information
- Identity provider certificate (add if certificate is not available or choose from drop down)
- Group attribute information
Trusted Connection supports (SAML) Security Assertion Mark-up Language integration is an authentication standard that allows for federated identity management and can support single sign-on (SSO), allowing users to authenticate via a SSO to their applications.
Trusted Connection supports Okta Identity Access Management as well as other identity providers (IDP),as part of the BYOID feature.
SAML without Active Directory configuration: if you are not using Active Directory, the specific steps and requirements will vary depending on the IDP you use. Refer to the documentation of the application for details and more information of how to find the information needed. However, the general process involved setting up SAML assertions and configuring the necessary metadata.
SAML with Active Directory configuration: When using Active Directory, you need to configure your Active Directory environment related fields and Trusted Connection to establish a connection between the two systems to configure appropriate settings for user attributes.
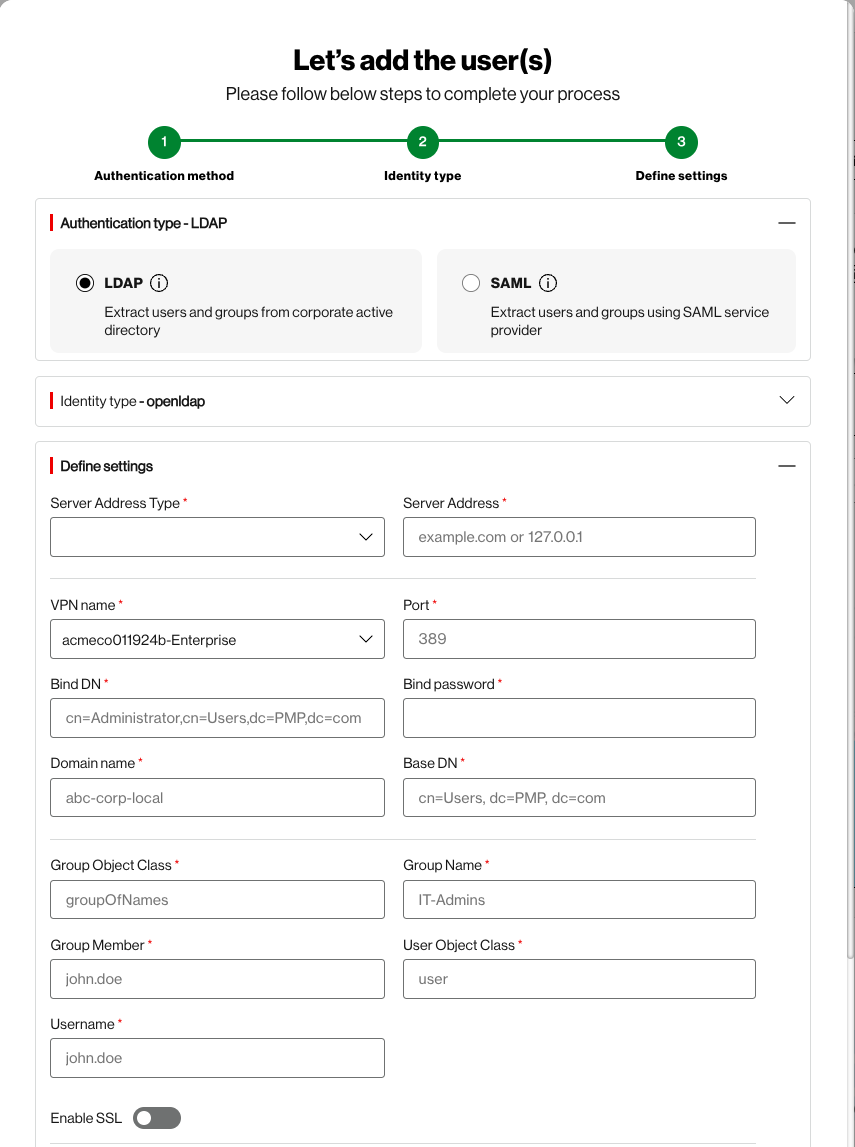
If you choose SAML with Active directory, you will need the following additional information. * are mandatory fields to make successful connections.
- Server Address Type*
- Server Address*
- VPN name*
- Port*
- Bind DN*
- Bind password *
- Domain name *
- Base DN *
- Group Object Class *
- Group Name *
- Group Member *
- User Object Class *
- Username *
- Enable SSL
- SSL mode *
- CA certificate *
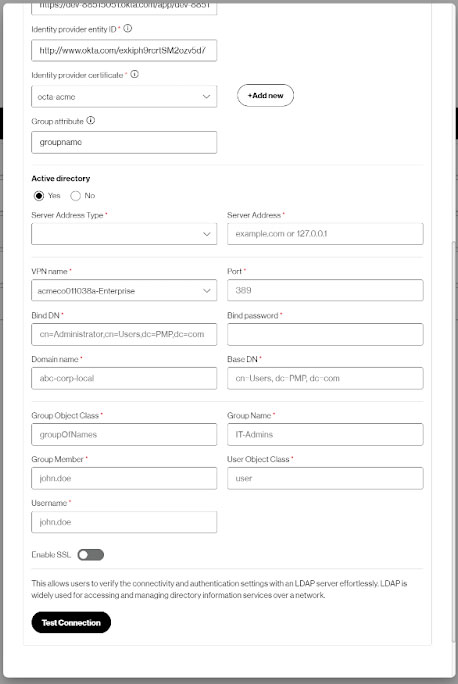
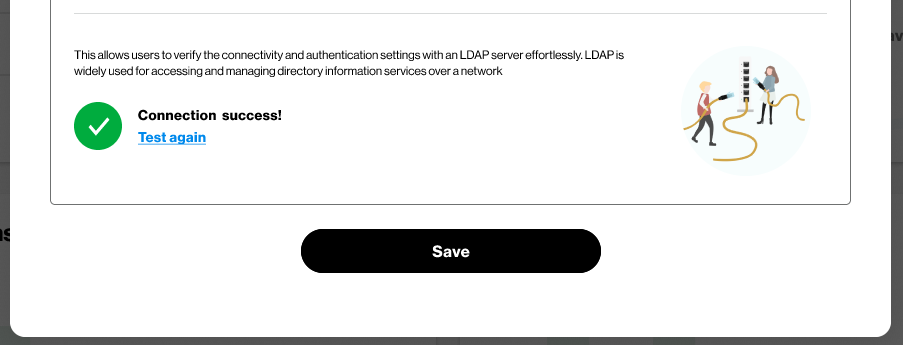
B. Then select “Test Connection”
After you receive “Successful connection” notification, click on save.
C. Select network security settings
Click “Proceed” under Network securing settings.
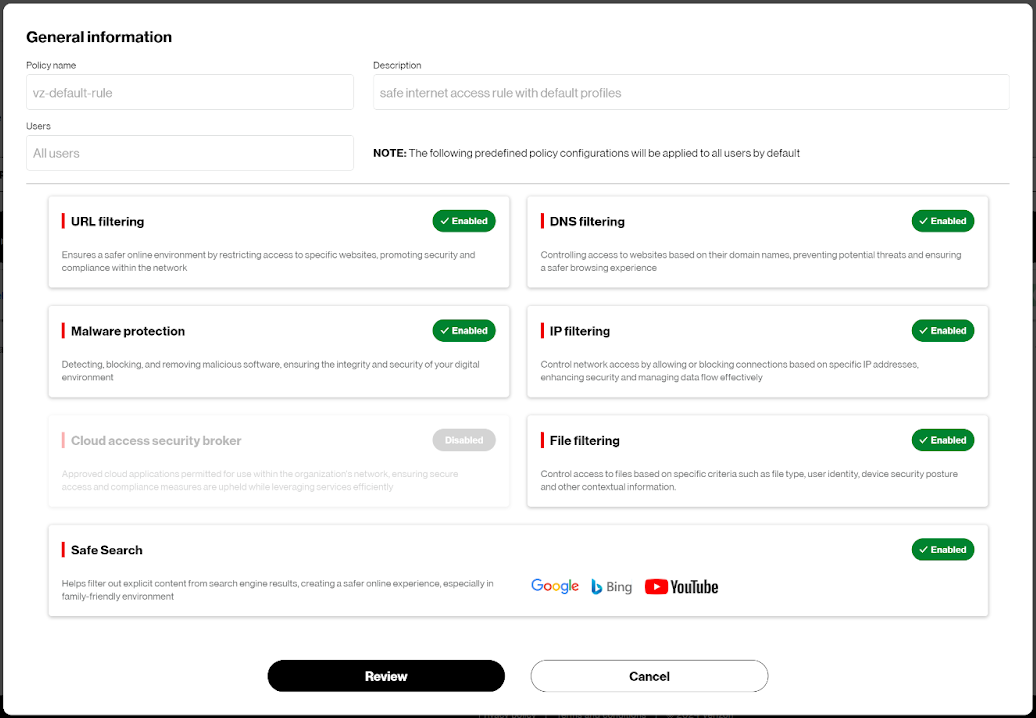
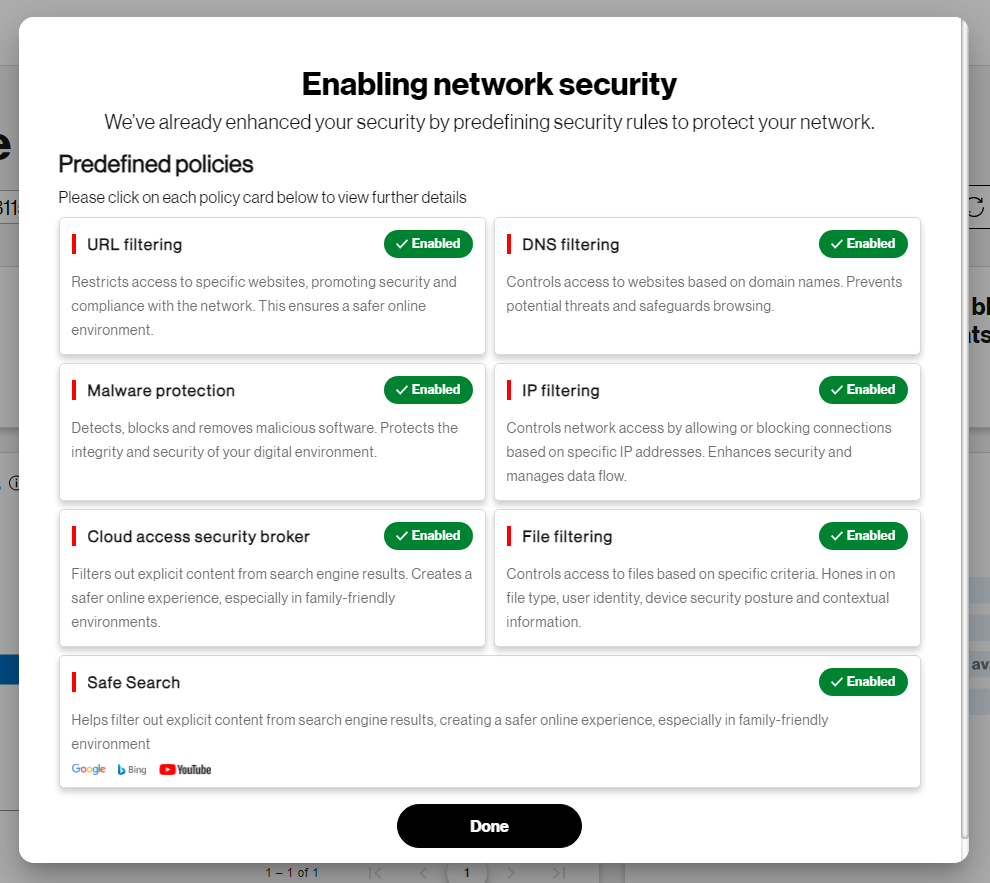
By default, Trusted Connection provides a set of predefined security rules to help protect your network against threats. These rules can be customized to your requirements from the Trusted Connection dashboard after initial setup is completed.
URL Filtering – Restricts access to specific websites promoting security and compliance
DNS Filtering – Controls access to websites based on their domain names to help protect against phishing attacks and other cyberthreats.
Malware Protection – Detects, blocks and removes malicious software
IP Filtering – Blocks access to specific IP addresses based on IP reputation
File Filtering – Controls access to files based on specific criteria such as file type, user identity, device security posture and other contextual information
SafeSearch – Helps filter out explicit content from search engine results
Cloud access security broker (CASB) – Implements zero-trust access control and policy enforcement for cloud SaaS applications (Trusted Connection Plus only)
Select “Done” on this screen:
Trusted Connection
Trusted Connection Plus
Secure Agent Access
Set up policies for each Operating System to manage the compliance of your devices. Policy options are OS specific. See the Windows example below.
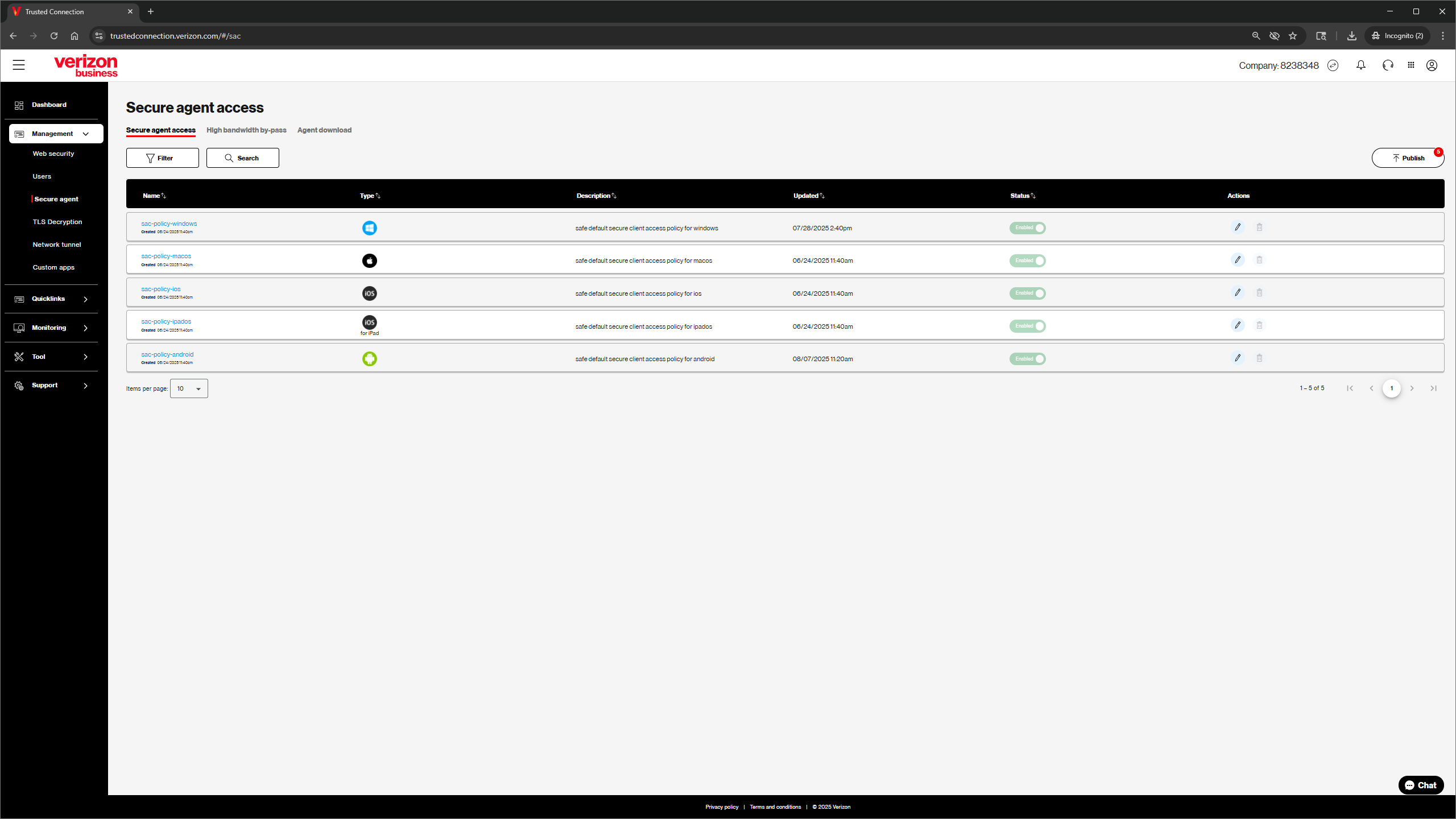
Policy Selections Include:
Manage devices only: When enabled, requires devices to be managed
Firewall: When enabled, requires devices to utilize firewall protection
Anti-malware: When enabled, requires devices to run anti-malware protection
Browser: When enabled, requires devices to run default browser (eg., Windows: Edge)
Disk Encryption: When enabled, requires devices to run disk encryption protection
Anti-phishing: When enabled, requires devices to run anti-phishing protection
Windows restriction: When enabled, requires devices to run specified OS versions. The “To” field can be blank to accept all future OS versions.
Secured Trusted Connection Agent Control - Always On: When enabled, requires devices to have a Trusted Connection Agent turned Always ‘ON’ Always in order to access resources
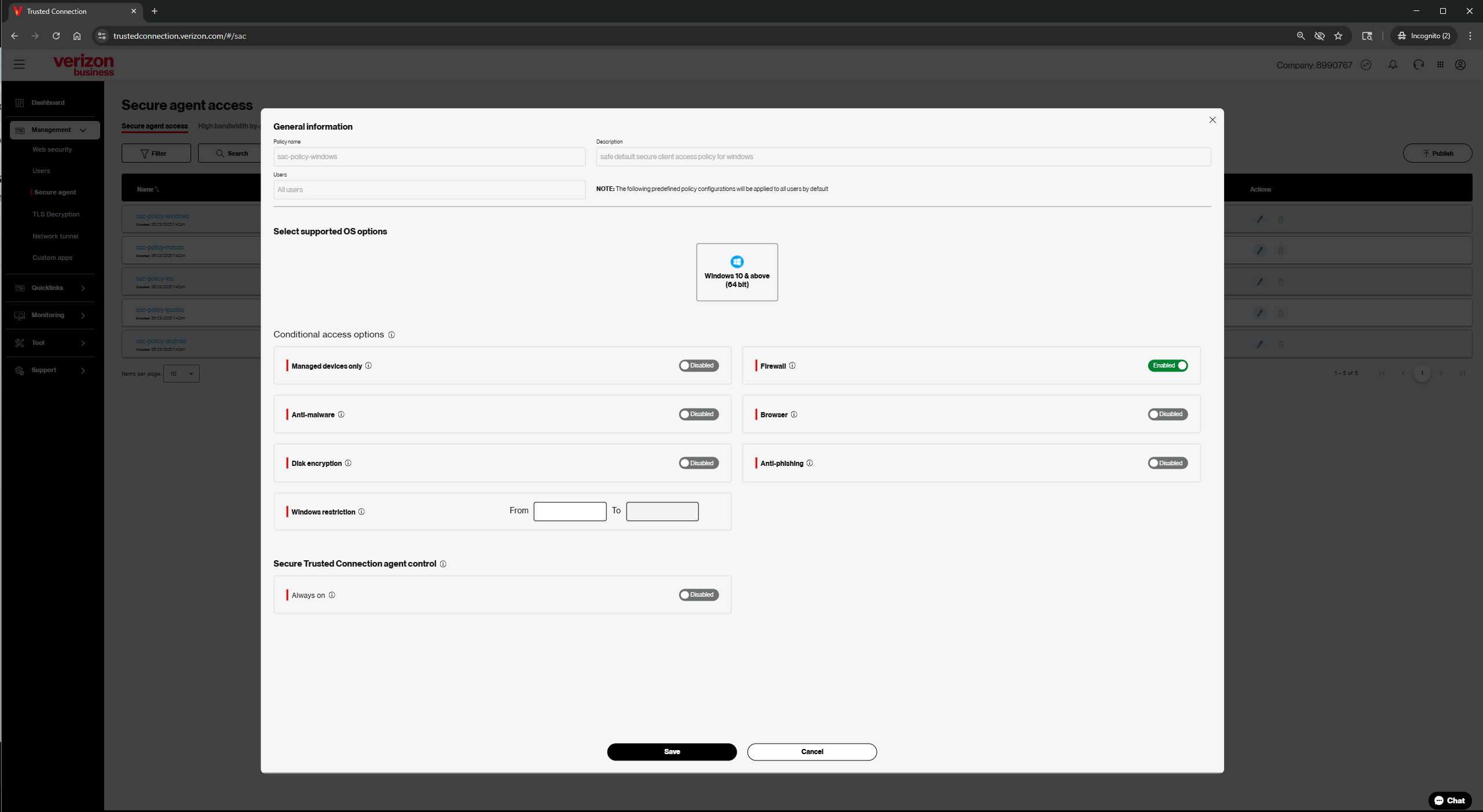
Monitoring your Device Compliance
This section will help the Administrator understand which users and devices are out of compliance so they can assist if necessary to restore compliance
Go to: Monitoring > Logs>Secure Agent Logs in the left hand navigation
Secure Agent Logs:
Will provide information on which devices are currently out of compliance
Details Included (from left to right)
- Date/Time
- Gateway
- User
- Device Name
- OS Type
- Action
- Allow - Device is connected and compliant
- Deny - Device is connected but NOT compliant
- Not connected - Device cannot connect to the agent
NOTE: All ‘Allow’ will appear with a green bar on the left hand side of the table
All ‘Deny’ will appear with a red bar on the left hand side of the table
All ‘Not Connected’ will appear without any colored bar on the left hand side
- End Point Secure IP: Point of Agent Connection
- End Point Public IP: Point of Internet Connection
- Failure Reason: Reason why device connection is denied
- DTP Policy Name: Policy related to failure to connect
Note: The ‘search’ feature will only include records that appear on screen. The number of records that can be selected to appear is located at the bottom left called ‘Items per page’. You can choose between 10-100 (even if there are hundreds of records in total). The only way to filter for all records is to download the log and then apply your own filter.
Install and Configure Agent
Select “Proceed”to install and configure the Trusted Connection agent
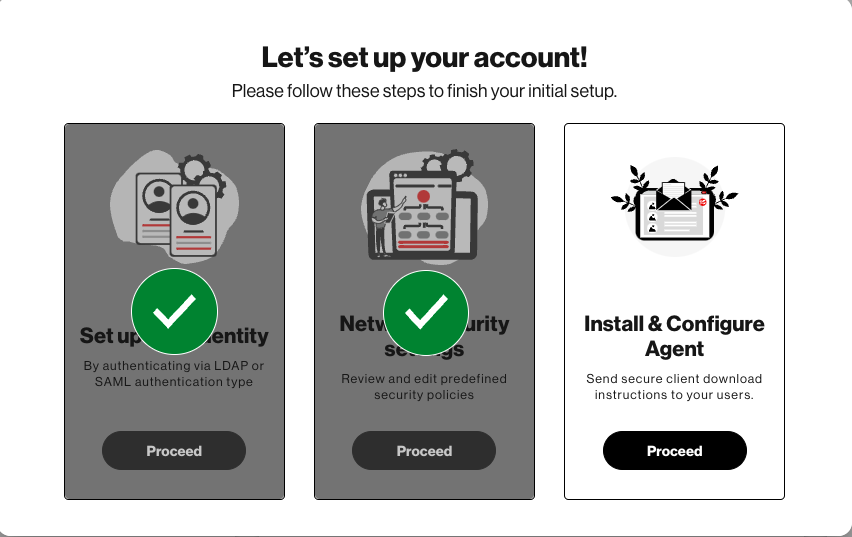
Choose “With MDM” or “No MDM” (or Do it later):
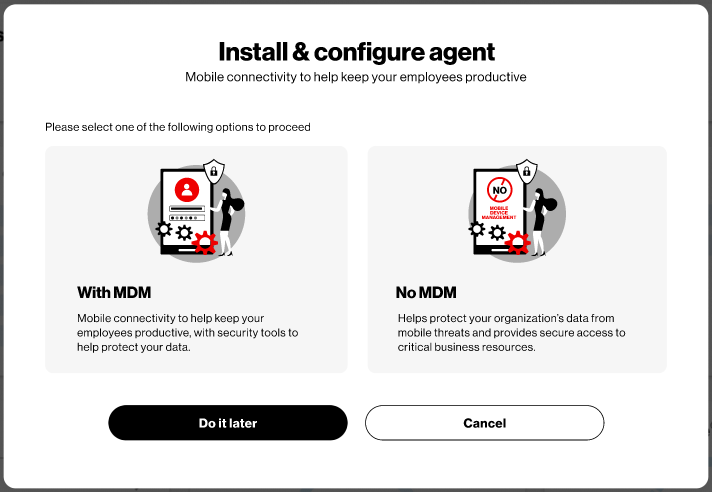
With MDM Option:
Select “Verizon MDM” or “Other MDM” and follow the instructions provided:Once you have completed the steps for MDM, select “Done”
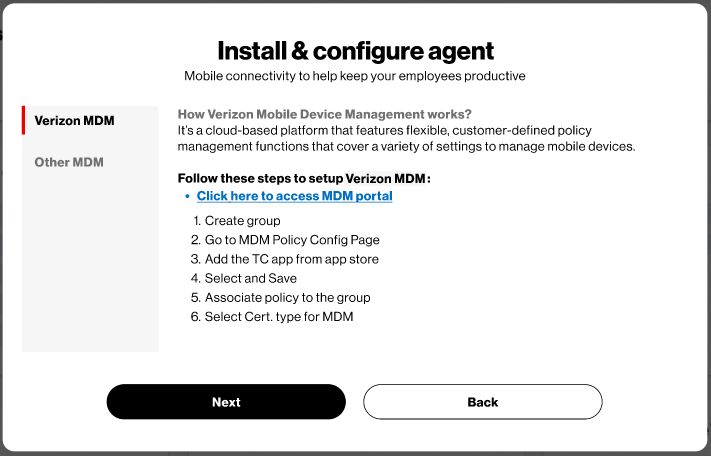
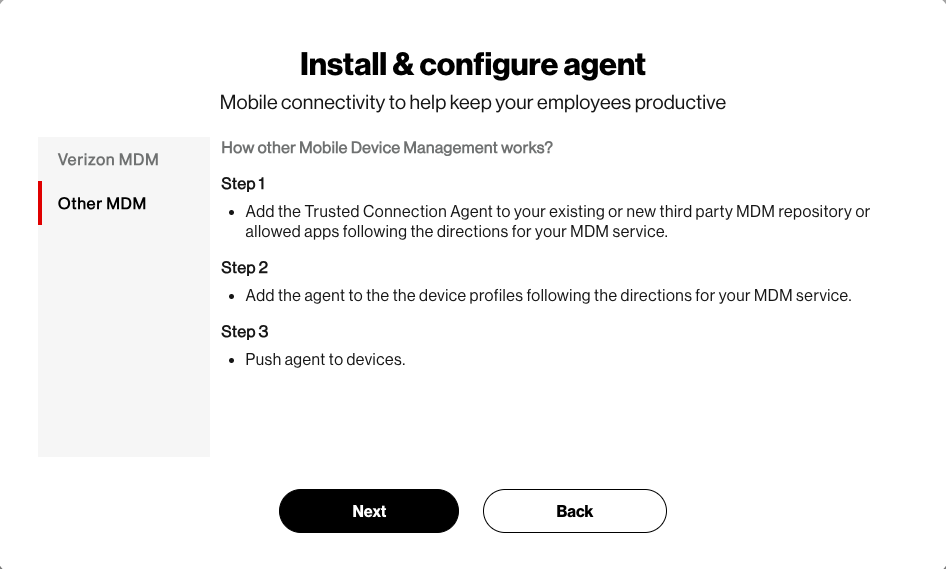
Once you have completed the steps for MDM, select “Done”
Without MDM Option:
Trusted Connection is designed to work with an MDM, either the Verizon MDM solution or other third party MDMs. If you do not presently have an MDM, please contact your sales representative to find out how to add the Verizon MDM. If you do not wish to use an MDM at this point, Trusted Connection will provide an email template to the customer administrator, with instructions on how to distribute agent download links to their organization's employees. The email will include links to agent downloads for various operating systems (Windows, iOS, iPadOS, macOS, and Android).
Note: If you choose to not use an MDM, your end users will have to install the agent on their devices, which involves several steps to complete.
That’s it – you are ready to explore the Trusted Connection dashboard. Click “Done”.
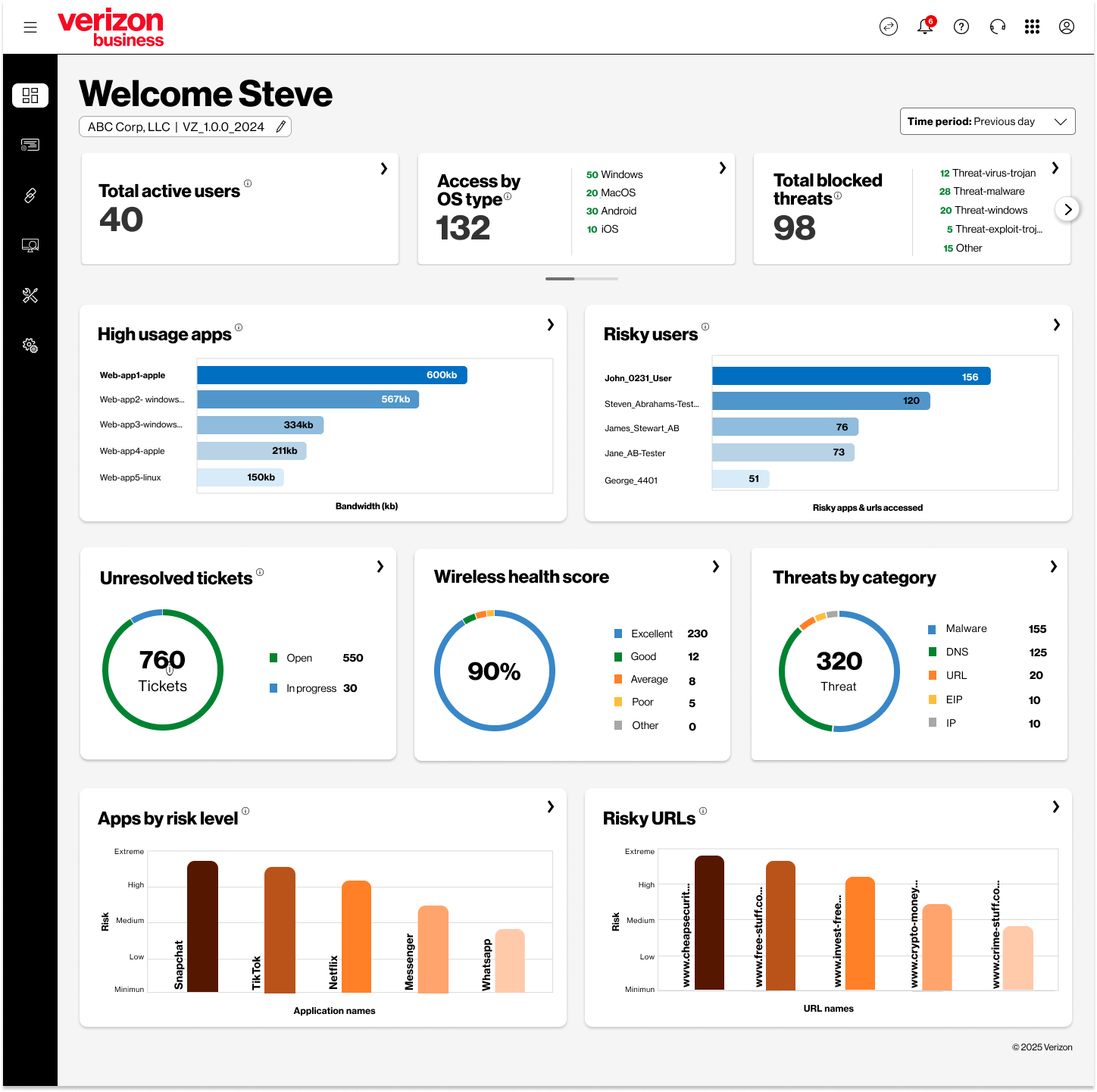
Trusted Connection Dashboard
The Trusted Connection dashboard provides a snapshot of your network and security analytics. Please note that any end user data will only appear after users download, install and activate the Verizon Trusted Connection client on their devices.
Trusted Connection Management
Trusted Connection Administrators are able make changes to the security settings and manage the service in a variety of ways:
Web Security settings allow you to further configure the preset rules applied upon initial setup. To modify these default policies, select the pencil icon under Actions for Verizon Default Security Rules.
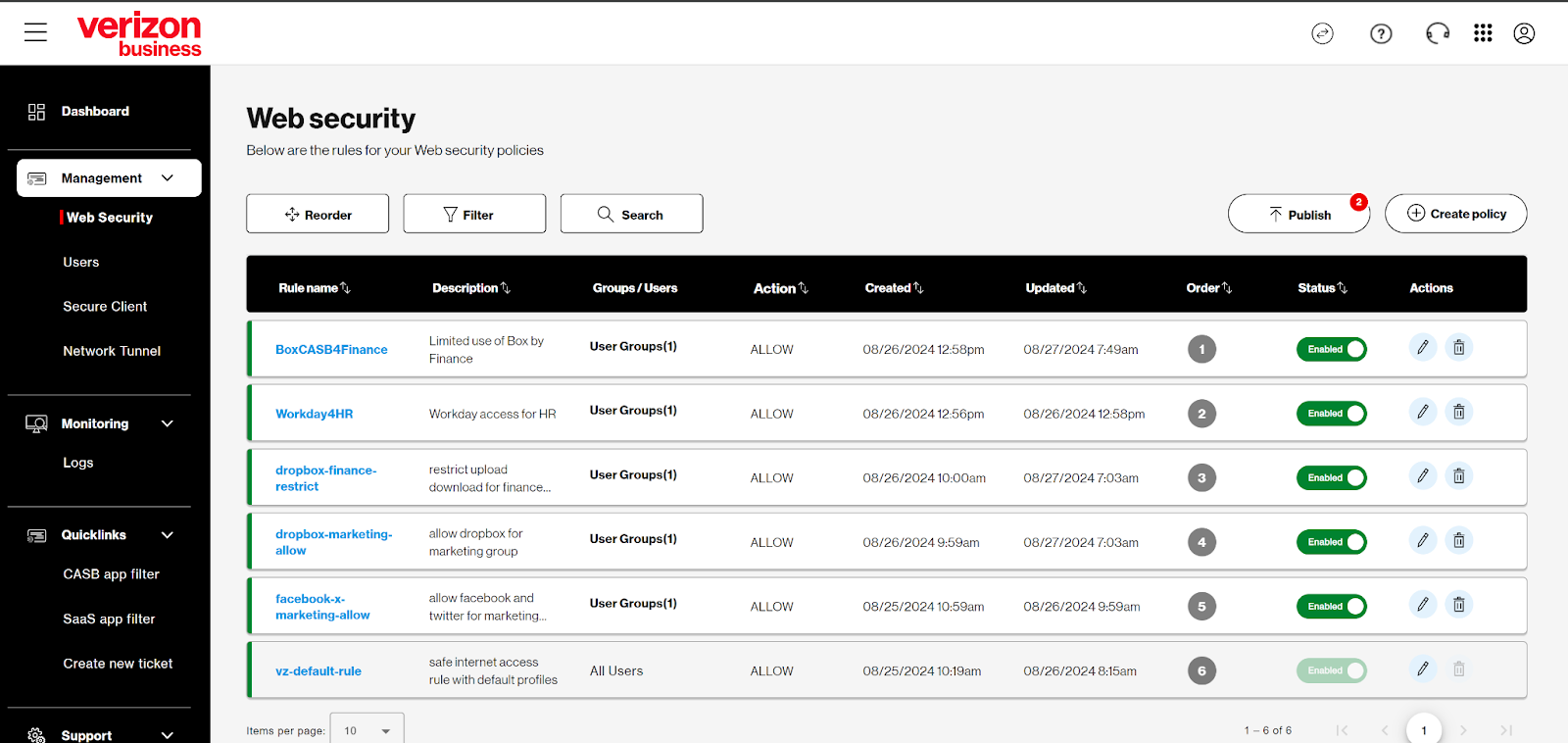
Click the “Review” button to review/edit all web security policies, or click the green “Enabled” button to edit specific web security policies.
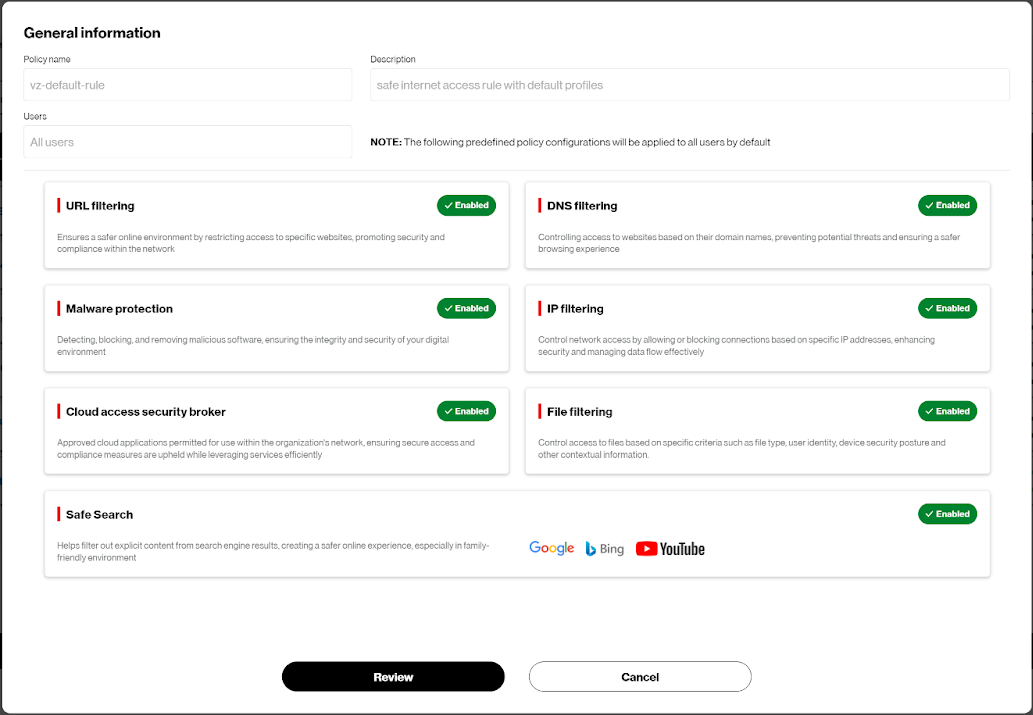
Note: Predefined security policy settings are applied to all users by default. Trusted Connection Plus customers have the option to apply security policies to specific users/groups.
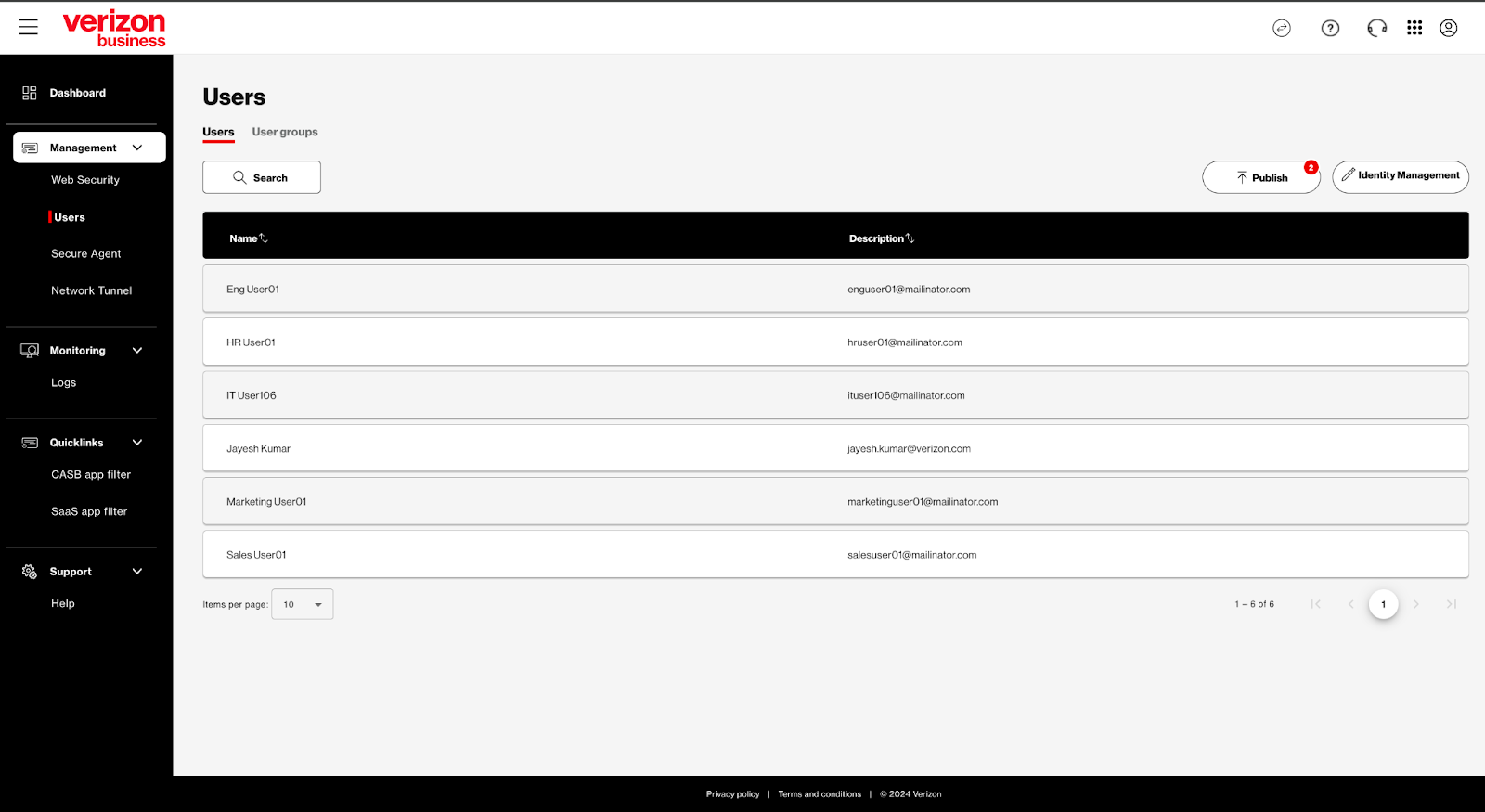
Users allow you to view users and user groups using the data that is synched with your LDAP enabled IDP.
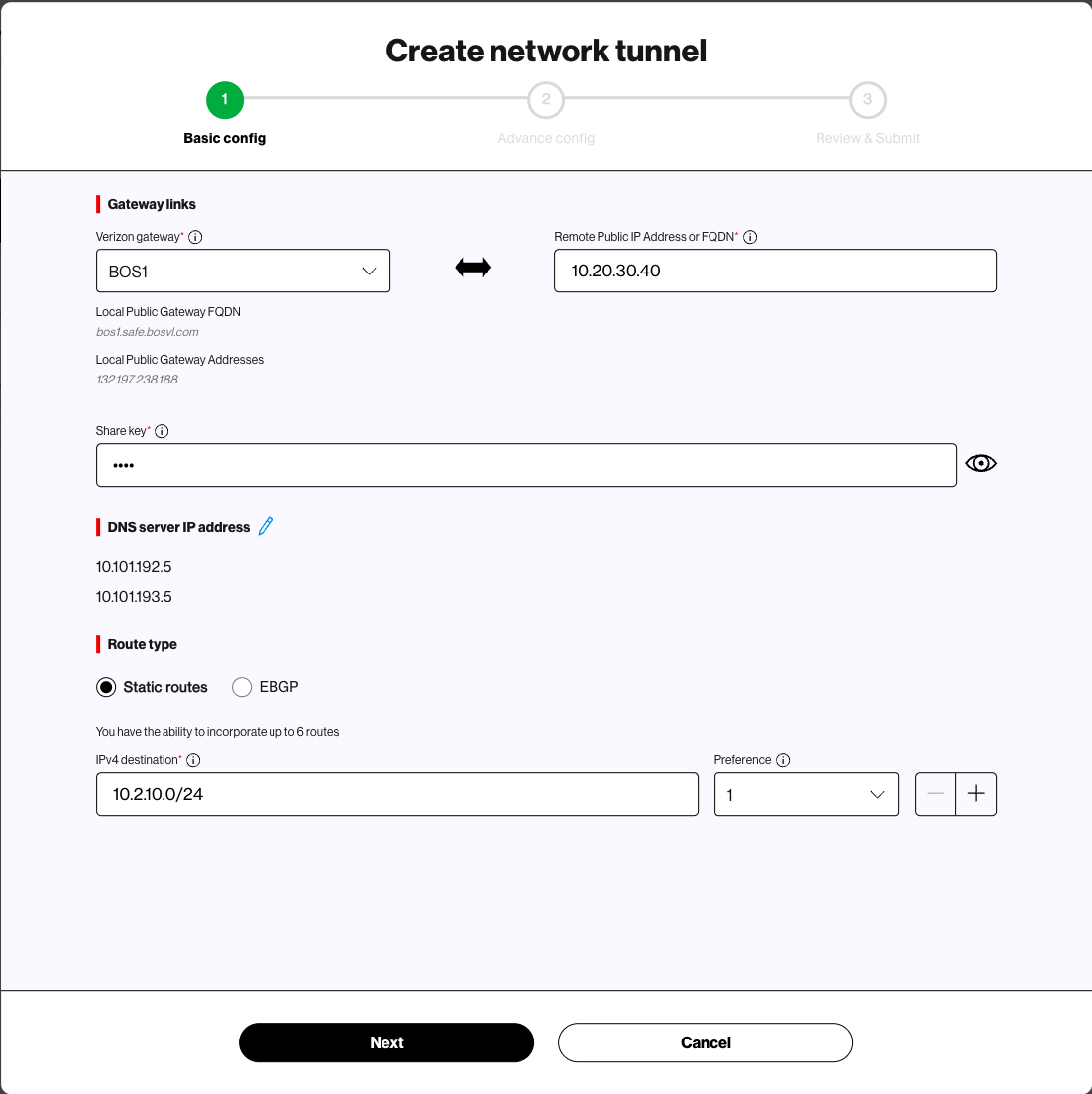
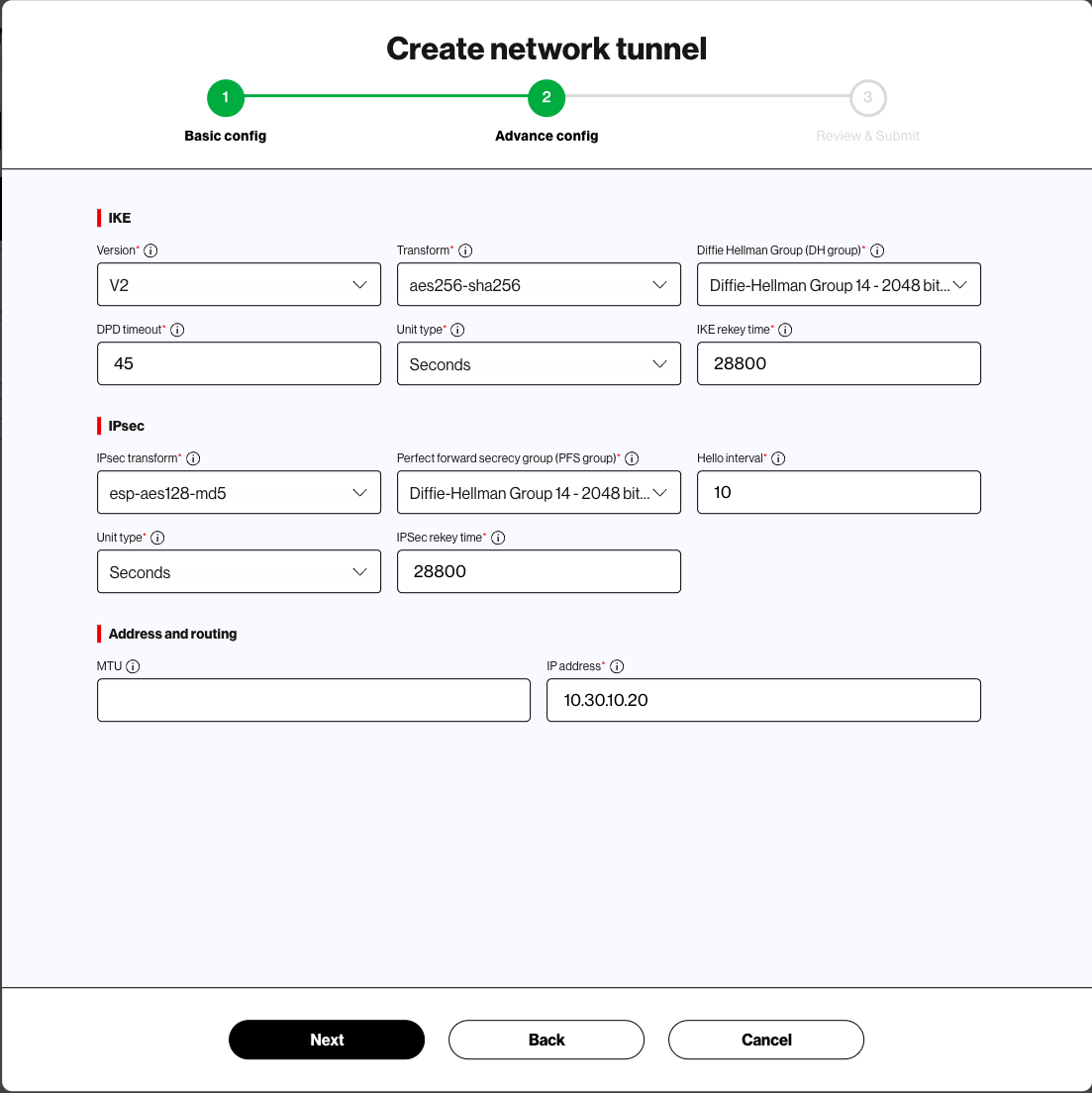
Network tunnel – Set up or modify an encrypted IPSEC tunnel to permit private traffic from end user devices to the Verizon Gateway for inspection.
Administrators can create up to two network tunnels by default. With a Plus subscription, administrators can create up to eight tunnels to accommodate their organization's specific networking requirements.
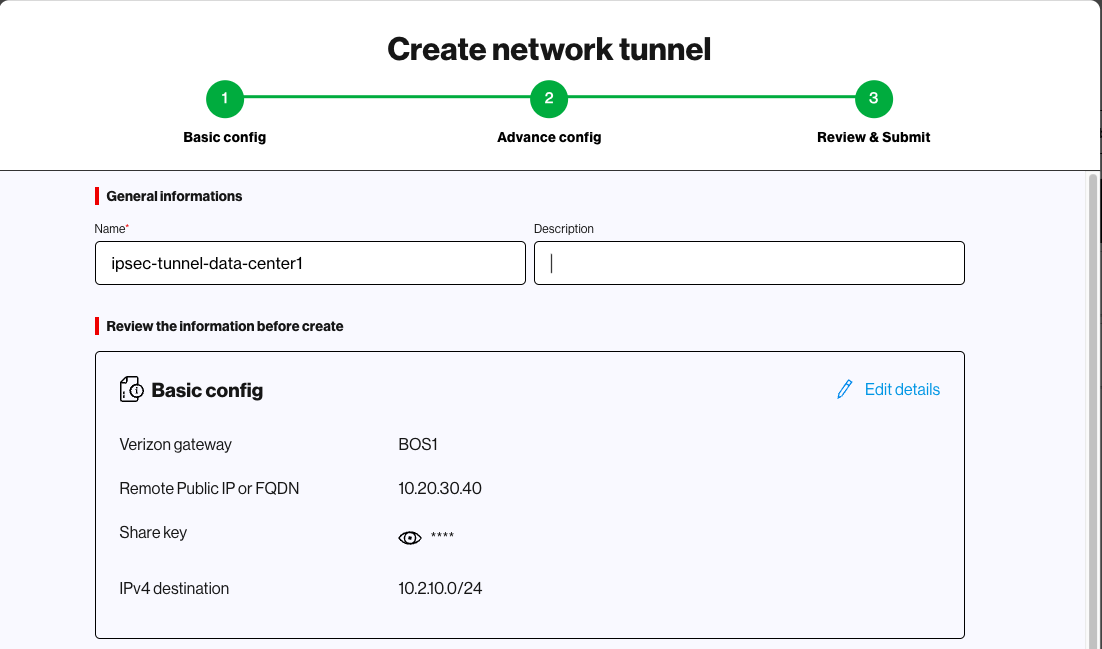
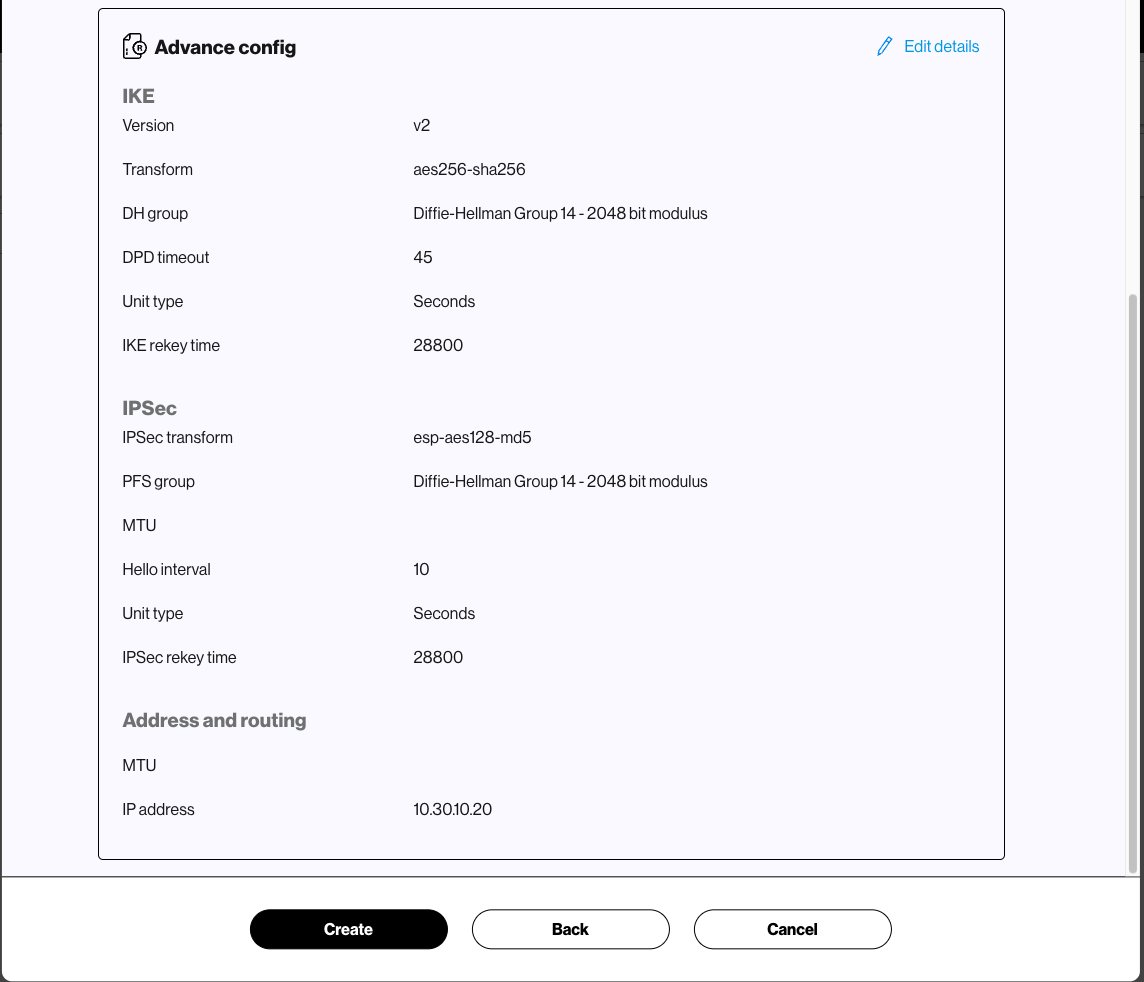
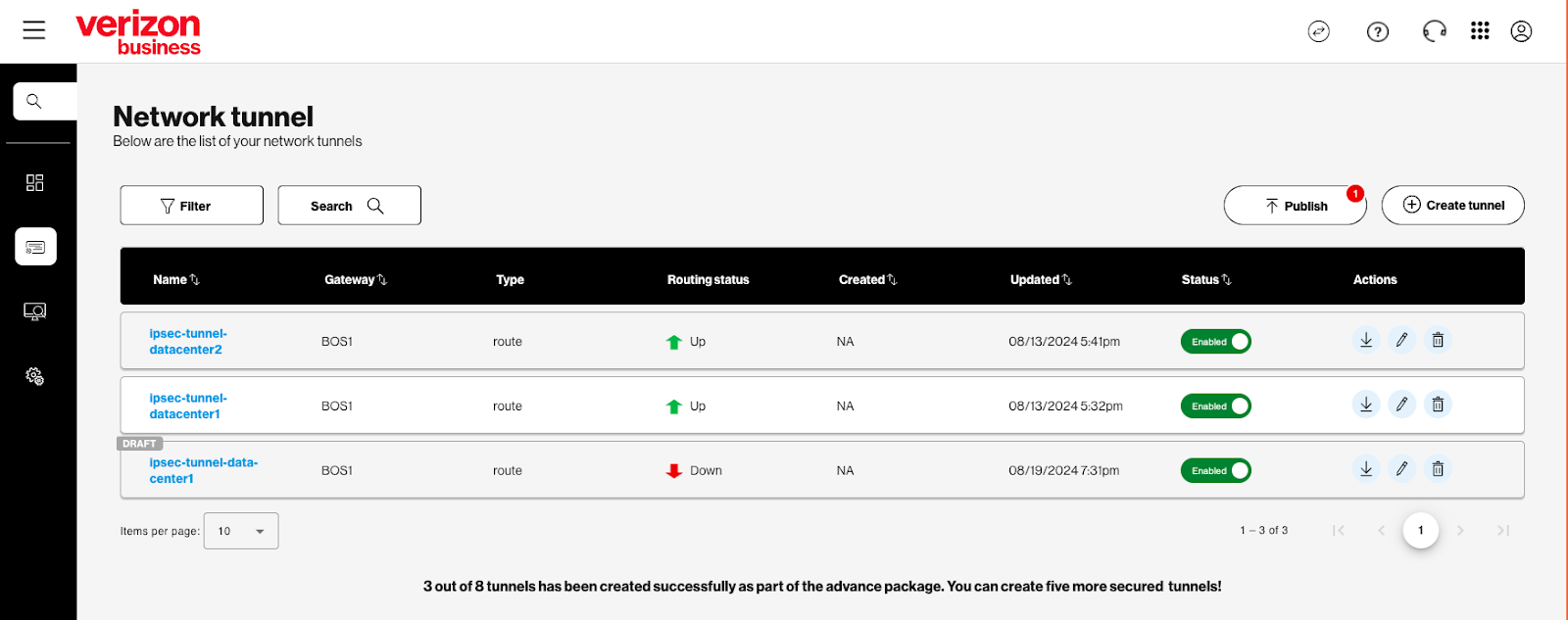
Trusted Connection Monitoring
Displays key information such as site health, threats, risky URLs, user data, device data, and logs. Drill downs into each area are available within the Trusted Connection portal.
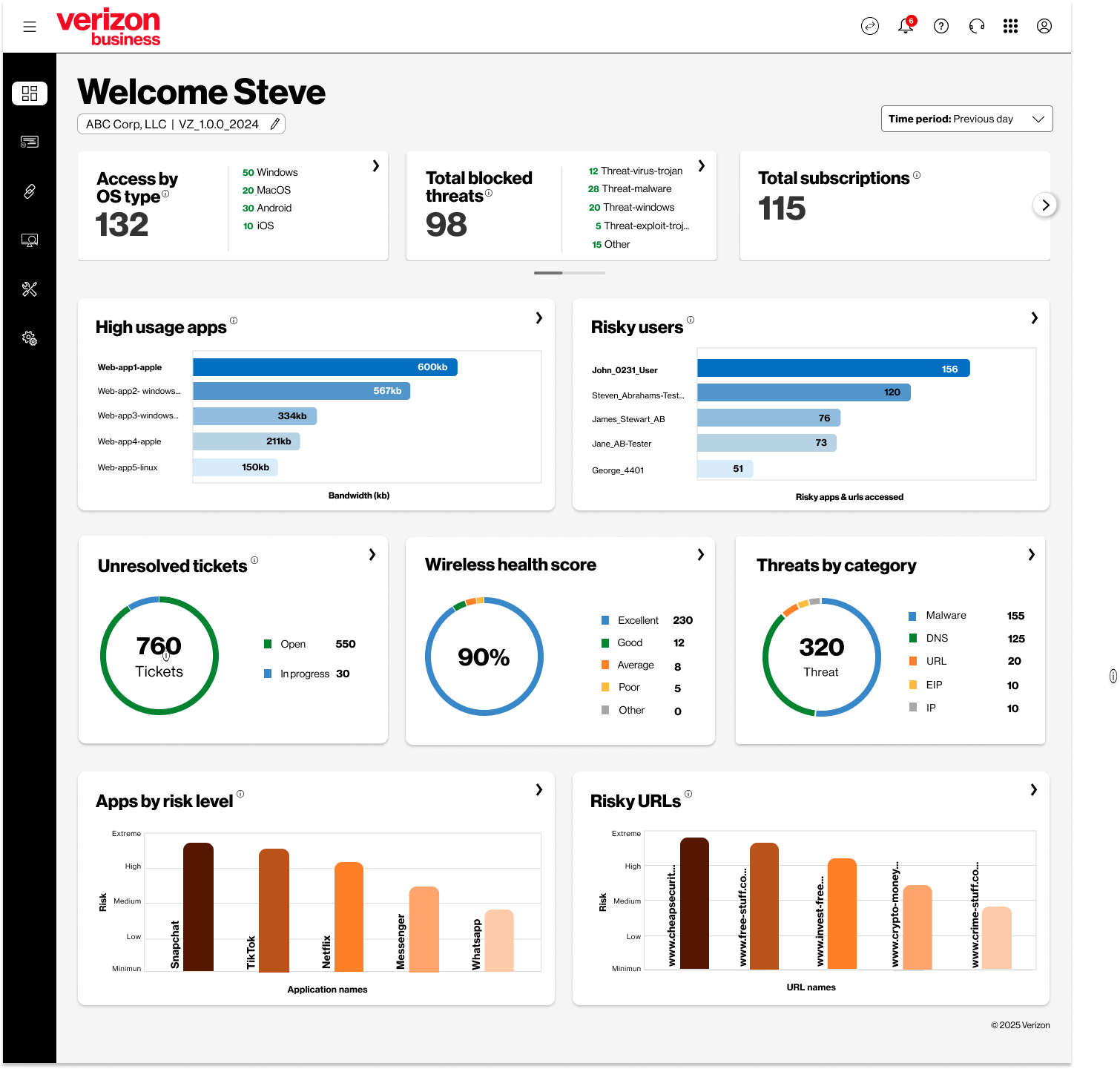
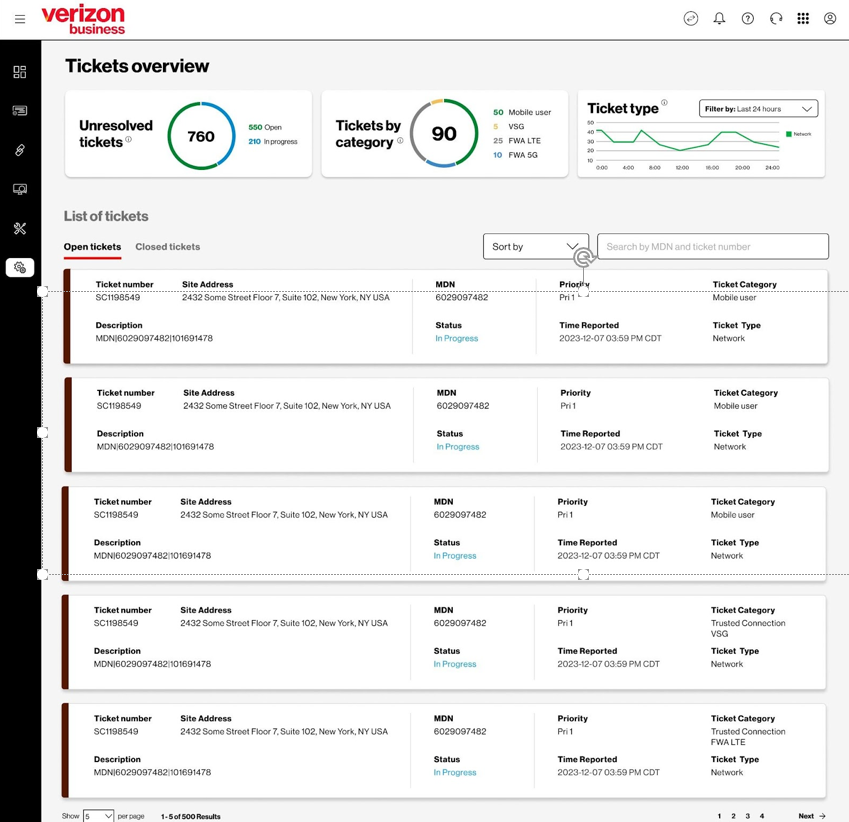
Trusted Connection Tickets Overview
The Tickets Overview screen will show you a list of open or closed tickets. On the ticket list you will see summaries at the top along with a filter to limit the time frame shown. Use the plus sign to see more information about that ticket and under the description select view details for even more. Open tickets are shown by default and you can get a closed ticket list as well by selecting that option.
Identity Management Systems (IDM) and Mobile Device Management (MDM) setup
Please read this linked document, which is designed to help Trusted Connection users with their service onboarding process. Trusted Connection users will be using an Identity Management System (IDM) and it is recommended the use of a Mobile Device Management (MDM) software too (view the FAQ for all IDM/MDM documents). The intent is to support the process of using the setup wizard built into the Trusted Connection Portal to configure Trusted Connection so that it will sync to the existing IDM and MDM software. While it covers some of the most popular used applications, it is not intended to be a comprehensive guide for setting up all the IDM or MDM applications that might be used in the market.
Customer Service
Technical Support
Please contact: 800.922.0204
Billing Questions
Please contact: 800.922.0204
Why Verizon
Verizon is a proven network security leader with 30+ years experience delivering and managing and securing complex global networks.
Performance, Reliability and Security
Verizon’s award-winning, reliable, secure nationwide 4G LTE & 5G network available in a variety of speeds to meet your business needs. FIOS is the ultra-fast fiber-optic connection with 99.99% network reliability.
Simplicity
Trusted Connection provides simple step-by-step instructions to get your business up and running with zero-trust connectivity quickly. Preset security options make it simple to get started by providing options to customize the service for your business.
Peace of Mind
Verizon is there for your business. In the event of a ransomware attack or data breach, Trusted Connection customers will have the option to quickly engage highly skilled security professionals via a 24/7 hotline for emergency service support.
